The Chinese point out-sponsored group known as UNC3886 has been discovered to exploit a zero-day flaw in VMware ESXi hosts to backdoor Windows and Linux units.
The VMware Equipment authentication bypass vulnerability, tracked as CVE-2023-20867 (CVSS rating: 3.9), “enabled the execution of privileged commands throughout Windows, Linux, and PhotonOS (vCenter) guest VMs without having authentication of visitor credentials from a compromised ESXi host and no default logging on guest VMs,” Mandiant reported.
UNC3886 was initially documented by the Google-owned danger intelligence organization in September 2022 as a cyber espionage actor infecting VMware ESXi and vCenter servers with backdoors named VIRTUALPITA and VIRTUALPIE.

Earlier this March, the team was joined to the exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS functioning method to deploy implants on the network appliances and interact with the aforementioned malware.
The menace actor has been explained as a “very adept” adversarial collective concentrating on defense, technology, and telecommunication companies in the U.S., Japan, and the Asia-Pacific area.
“The group has access to substantial study and help for comprehending the fundamental technology of appliances becoming focused,” Mandiant researchers stated, calling out its pattern of weaponizing flaws in firewall and virtualization computer software that do not assistance EDR remedies.
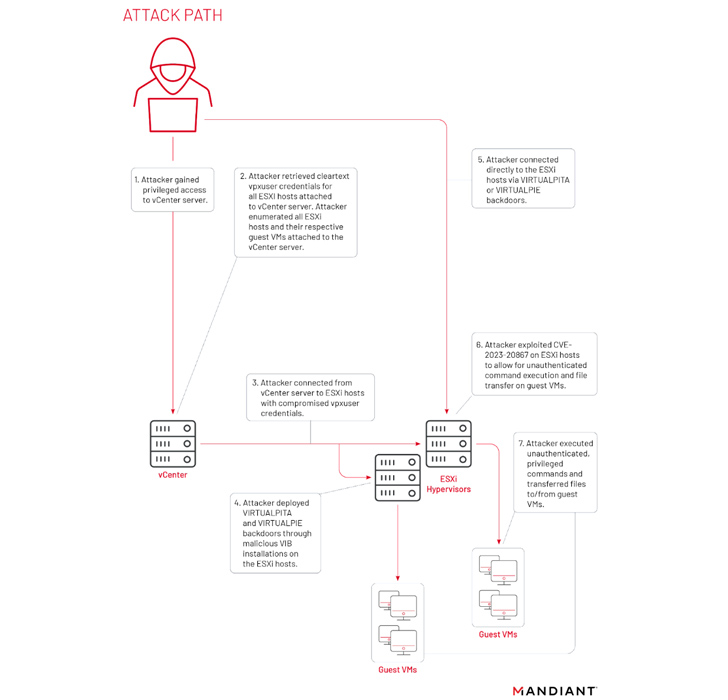
As component of its attempts to exploit ESXi units, the threat actor has also been noticed harvesting credentials from vCenter servers as effectively as abusing CVE-2023-20867 to execute commands and transfer files to and from guest VMs from a compromised ESXi host.
A noteworthy factor of UNC3886’s tradecraft is its use of Virtual Equipment Interaction Interface (VMCI) sockets for lateral movement and continued persistence, therefore enabling it to build a covert channel between the ESXi host and its visitor VMs.
Future WEBINAR🔐 Mastering API Security: Knowledge Your Accurate Attack Surface area
Discover the untapped vulnerabilities in your API ecosystem and consider proactive measures in direction of ironclad security. Be a part of our insightful webinar!
Be a part of the Session.wn-button,.wn-label,.wn-label:followingshow:inline-block.test_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-suitable-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimension:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.wn-label:afterwidth:50pxheight:6pxcontent:”border-best:2px strong #d9deffmargin: 8px.wn-titlefont-dimension:21pxpadding:10px 0font-body weight:900text-align:leftline-peak:33px.wn-descriptiontext-align:leftfont-size:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-color:#4469f5font-size:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-weight:500letter-spacing:.2px
“This open communication channel amongst visitor and host, where by both position can act as shopper or server, has enabled a new implies of persistence to get back accessibility on a backdoored ESXi host as very long as a backdoor is deployed and the attacker gains original obtain to any visitor device,” the company mentioned.
The improvement will come as Summoning Group researcher Sina Kheirkhah disclosed a few distinct flaws in VMware Aria Functions for Networks (CVE-2023-20887, CVE-2023-20888, and CVE-2023-20889) that could outcome in remote code execution.
“UNC3886 proceeds to existing issues to investigators by disabling and tampering with logging expert services, selectively eradicating log gatherings connected to their activity,” it even further included. “The menace actors’ retroactive cleanup done in times of past public disclosures on their action signifies how vigilant they are.”
Observed this article fascinating? Abide by us on Twitter and LinkedIn to examine far more special material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Malicious Actors Exploit GitHub to Distribute Fake Exploits
Malicious Actors Exploit GitHub to Distribute Fake Exploits