The China-based menace actor identified as Mustang Panda is suspected to have targeted Myanmar’s Ministry of Defence and Overseas Affairs as component of twin strategies built to deploy backdoors and distant entry trojans.
The conclusions arrive from CSIRT-CTI, which mentioned the activities took area in November 2023 and January 2024 after artifacts in relationship with the assaults had been uploaded to the VirusTotal platform.
“The most popular of these TTPs are the use of respectable software package which includes a binary developed by engineering business Bernecker & Rainer (B&R) and a element of the Windows 10 enhance assistant to sideload destructive dynamic-hyperlink libraries (DLLs),” CSIRT-CTI stated.
Mustang Panda, lively since at minimum 2012, is also identified by the cybersecurity community underneath the names BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, Purple Lich, Stately Taurus, and TEMP.Hex.

In modern months, the adversary has been attributed to attacks targeting an unnamed Southeast Asian authorities as very well as the Philippines to provide backdoors capable of harvesting delicate details.
The November 2023 an infection sequence begins with a phishing email bearing a booby-trapped ZIP archive attachment made up of a respectable executable (“Investigation of the 3rd assembly of NDSC.exe”) that’s at first signed by B&R Industrial Automation GmbH and a DLL file (“BrMod104.dll”).
The attack normally takes benefit of the fact that the binary is susceptible to DLL research buy hijacking to facet-load the rogue DLL and subsequently build persistence and get in touch with with a command-and-command (C2) server and retrieve a recognized backdoor referred to as PUBLOAD, which, in turn, functions as a custom loader to fall the PlugX implant.
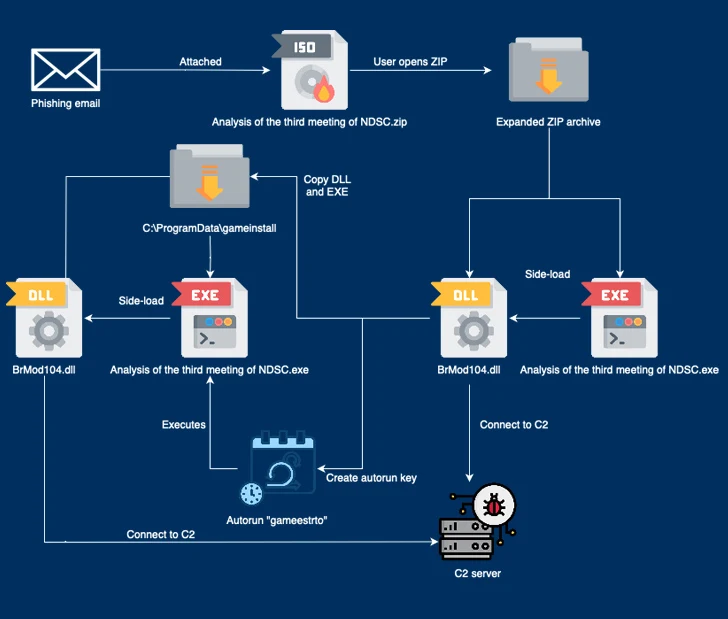
“The risk actors endeavor to disguise the [C2] visitors as Microsoft update visitors by including the ‘Host: www.asia.microsoft.com’ and ‘User-Agent: Windows-Update-Agent’ headers,” CSIRT-CTI mentioned, mirror a May well 2023 campaign disclosed by Lab52.
On the other hand, the next campaign noticed earlier this month employs an optical disc impression (“ASEAN Notes.iso”) made up of LNK shortcuts to set off a multi-stage approach that makes use of a different bespoke loader named TONESHELL to most likely deploy PlugX from a now-inaccessible C2 server.

It truly is really worth noting that a similar attack chain attributed to Mustang Panda was beforehand unearthed by EclecticIQ in February 2023 in intrusions aimed at govt and community sector organizations across Asia and Europe.
“Next the rebel assaults in northern Myanmar [in October 2023], China has expressed issue with regards to its result on trade routes and security close to the Myanmar-China border,” CSIRT-CTI claimed.
“Stately Taurus operations are known to align with geopolitical pursuits of the Chinese federal government, like many cyberespionage operations towards Myanmar in the earlier.”
Discovered this write-up intriguing? Abide by us on Twitter and LinkedIn to examine extra exceptional material we post.
Some parts of this article are sourced from:
thehackernews.com


 493 Companies Share Their SaaS Security Battles – Get Insights in this WebinarJan 29, 2024SaaS Security / Webinar In today's digital world, security risks are more prevalent than ever, especially when it comes to Software as a Service (SaaS) applications. Did you know that an alarming 97% of companies face serious risks from unsecured SaaS applications? Moreover, about 20% of these organizations are struggling with internal data threats. These statistics aren't just numbers; they're a wake-up call. We're excited to invite you to a not-to-be-missed webinar, " Critical SaaS Security Do's and Don'ts: Insights from 493 Companies ," with Ran Senderovitz , the Chief Operating Officer of Wing Security. Ran isn't just going to talk about the problems; he's going to dive deep into the realities of SaaS security, backed by extensive research and data analysis from almost 500 companies using SaaS. Here's What This Webinar Offers: Insights Across Data, SaaS Applications, Users, and AI: Explore a comprehensive analysis of the statistics about SaaS security, di
493 Companies Share Their SaaS Security Battles – Get Insights in this WebinarJan 29, 2024SaaS Security / Webinar In today's digital world, security risks are more prevalent than ever, especially when it comes to Software as a Service (SaaS) applications. Did you know that an alarming 97% of companies face serious risks from unsecured SaaS applications? Moreover, about 20% of these organizations are struggling with internal data threats. These statistics aren't just numbers; they're a wake-up call. We're excited to invite you to a not-to-be-missed webinar, " Critical SaaS Security Do's and Don'ts: Insights from 493 Companies ," with Ran Senderovitz , the Chief Operating Officer of Wing Security. Ran isn't just going to talk about the problems; he's going to dive deep into the realities of SaaS security, backed by extensive research and data analysis from almost 500 companies using SaaS. Here's What This Webinar Offers: Insights Across Data, SaaS Applications, Users, and AI: Explore a comprehensive analysis of the statistics about SaaS security, di