Government and telecom entities have been subjected to a new wave of attacks by a China-connected menace actor tracked as Budworm using an up-to-date malware toolset.
The intrusions, concentrating on a Center Eastern telecommunications organization and an Asian government, took area in August 2023, with the adversary deploying an enhanced model of its SysUpdate toolkit, the Symantec Danger Hunter Workforce, portion of Broadcom, reported in a report shared with The Hacker News.
Budworm, also referred to by the names APT27, Bronze Union, Emissary Panda, Iron Tiger, Lucky Mouse, and Pink Phoenix, is recognized to be lively given that at least 2013, targeting a wide vary of business verticals in pursuit of its intelligence collecting plans.
The country-condition group leverages several tools this sort of as China Chopper web shell, Gh0st RAT, HyperBro, PlugX, SysUpdate, and ZXShell to exfiltrate substantial-price data and preserve obtain to sensitive programs in excess of a long time period of time.

A former report from SecureWorks in 2017 unveiled the attacker’s penchant for amassing protection, security, and political intelligence from companies around the globe, characterizing it as a formidable menace.
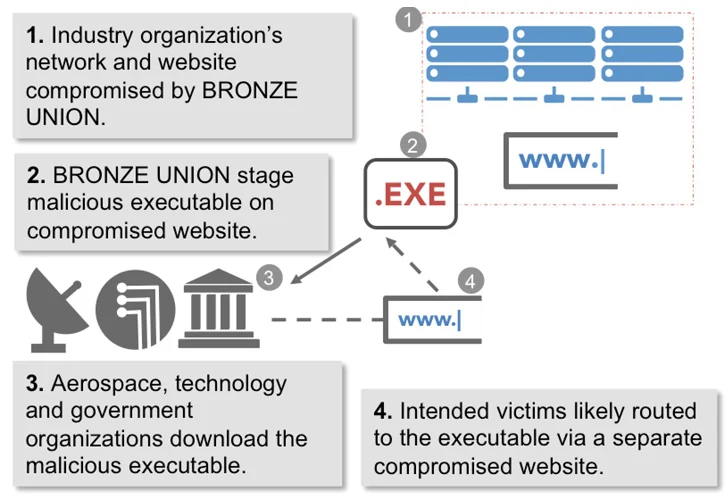
It has also been observed exploiting susceptible internet-struggling with solutions to gain access to targeted networks. Previously this March, Trend Micro shed mild on the Linux edition of SysUpdate, which packs in abilities to circumvent security program and resist reverse engineering.
The backdoor is aspect-abundant, generating it feasible to seize screenshots, terminate arbitrary procedures, conduct file operations, retrieve travel information and facts, and execute instructions.
“As nicely as its customized malware, Budworm also used a variety of residing-off-the-land and publicly accessible applications in these attacks,” Symantec mentioned. “It appears the exercise by the group might have been stopped early in the attack chain as the only malicious exercise seen on infected equipment is credential harvesting.”
Future WEBINARFight AI with AI — Battling Cyber Threats with Upcoming-Gen AI Equipment
All set to deal with new AI-pushed cybersecurity difficulties? Sign up for our insightful webinar with Zscaler to handle the escalating threat of generative AI in cybersecurity.
Supercharge Your Skills
With the most up-to-date enhancement, Budworm is the new addition to a expanding record of threat actors that have qualified their eyes on the telecom sector in the Middle East, such as previously undocumented clusters dubbed ShroudedSnooper and Sandman.
“SysUpdate has been in use by Budworm considering that at the very least 2020, and the attackers look to regularly develop the tool to enhance its abilities and stay away from detection.”
“That Budworm carries on to use a identified malware (SysUpdate), together with strategies it is recognized to favor, this kind of as DLL side-loading using an application it has utilised for this purpose in advance of, show that the team is just not too concerned about obtaining this activity affiliated with it if it is found.”
Located this article attention-grabbing? Follow us on Twitter and LinkedIn to study much more special content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Update Chrome Now: Google Releases Patch for Actively Exploited Zero-Day Vulnerability
Update Chrome Now: Google Releases Patch for Actively Exploited Zero-Day Vulnerability