
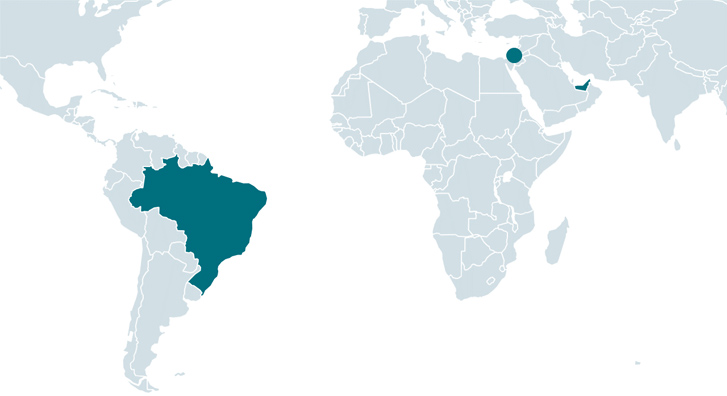
The Iranian threat actor acknowledged as Charming Kiten has been linked to a new wave of assaults targeting distinct entities in Brazil, Israel, and the U.A.E. working with a previously undocumented backdoor named Sponsor.
Slovak cybersecurity agency is monitoring the cluster less than the identify Ballistic Bobcat. Victimology patterns advise that the team mostly singles out education and learning, authorities, and healthcare organizations, as perfectly as human rights activists and journalists.
At minimum 34 victims of Sponsor have been detected to day, with the earliest situations of deployment dating back to September 2021.
“The Sponsor backdoor utilizes configuration information saved on disk,” ESET researcher Adam Burgher mentioned in a new report printed nowadays. “These documents are discreetly deployed by batch files and deliberately made to look innocuous, therefore making an attempt to evade detection by scanning engines.”
Impending WEBINARWay Way too Vulnerable: Uncovering the Condition of the Identification Attack Surface
Attained MFA? PAM? Services account protection? Discover out how perfectly-geared up your corporation definitely is towards identity threats
Supercharge Your Competencies
The campaign, dubbed Sponsoring Access, consists of acquiring first entry by opportunistically exploiting recognised vulnerabilities in internet-exposed Microsoft Exchange servers to conduct article-compromise steps, echoing an advisory issued by Australia, the U.K., and the U.S. in November 2021.
In one particular incident specific by ESET, an unknown Israeli corporation operating an insurance policies market is reported to have been infiltrated by the adversary in August 2021 to produce future-stage payloads this sort of as PowerLess, Plink, and a Go-primarily based open-supply write-up-exploitation toolkit referred to as Merlin over the future couple of months.
“The Merlin agent executed a Meterpreter reverse shell that identified as again to a new [command-and-control] server,” Burgher stated. “On December 12th, 2021, the reverse shell dropped a batch file, install.bat, and within minutes of executing the batch file, Ballistic Bobcat operators pushed their most recent backdoor, Sponsor.”
Composed in C++, Sponsor is developed to get host details and procedure recommendations obtained from a remote server, the effects of which are sent back again to the server. This incorporates command and file execution, file obtain, and update the checklist of attacker-controlled servers.
“Ballistic Bobcat continues to work on a scan-and-exploit design, hunting for targets of possibility with unpatched vulnerabilities in internet-exposed Microsoft Exchange servers,” Burgher explained. “The team continues to use a diverse open-supply toolset supplemented with various custom made programs, such as its Sponsor backdoor.”
Located this post interesting? Follow us on Twitter and LinkedIn to study more special information we publish.
Some parts of this article are sourced from:
thehackernews.com


 How to Prevent API Breaches: A Guide to Robust Security
How to Prevent API Breaches: A Guide to Robust Security