The Laptop Unexpected emergency Response Staff of Ukraine (CERT-UA) has warned of a new phishing campaign orchestrated by the Russia-joined APT28 team to deploy earlier undocumented malware this kind of as OCEANMAP, MASEPIE, and STEELHOOK to harvest delicate facts.
The action, which was detected by the agency among December 15 and 25, 2023, targets govt entities with email messages urging recipients to simply click on a connection to perspective a document.
Approaching WEBINAR From Person to ADMIN: Learn How Hackers Gain Complete Regulate
Learn the magic formula techniques hackers use to turn out to be admins, how to detect and block it right before it really is too late. Sign-up for our webinar currently.
Be part of Now
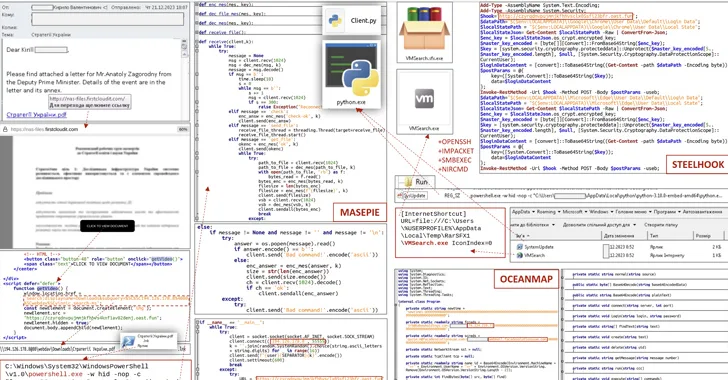
On the other hand, to the contrary, the one-way links redirect to destructive web means that abuse JavaScript and the “research-ms:” URI protocol handler to fall a Windows shortcut file (LNK) that launches PowerShell commands to activate an infection chain for a new malware recognised as MASEPIE.
MASEPIE is a Python-based tool to down load/upload information and execute commands, with communications with the command-and-manage (C2) server getting put over an encrypted channel applying the TCP protocol.
The assaults additional pave the way for the deployment of added malware, which include a PowerShell script known as STEELHOOK which is able of harvesting web browser info and exporting it to an actor-managed server in Foundation64-encoded format.
Also shipped is a C#-based backdoor dubbed OCEANMAP that is built to execute commands making use of cmd.exe.
“The IMAP protocol is utilised as a command channel,” CERT-UA mentioned, including persistence is realized by creating a URL file named “VMSearch.url” in the Windows Startup folder.
“Commands, in Foundation64-encoded variety, are contained in the ‘Drafts’ of the corresponding email directories every of the drafts consists of the identify of the laptop, the identify of the user and the version of the OS. The success of the instructions are stored in the inbox listing.”

The agency further more pointed out that reconnaissance and lateral motion pursuits are carried out within just an hour of the initial compromise by having advantage of applications like Impacket and SMBExec.
The disclosure will come weeks immediately after IBM X-Power disclosed APT28’s use of lures associated to the ongoing Israel-Hamas war to facilitate the supply of a custom made backdoor known as HeadLace.
In new weeks, the prolific Kremlin-backed hacking team has also been attributed to the exploitation of a now-patched critical security flaw in its Outlook email provider (CVE-2023-23397, CVSS score: 9.8) to achieve unauthorized accessibility to victims’ accounts inside Exchange servers.
Observed this report exciting? Follow us on Twitter and LinkedIn to examine additional exceptional articles we put up.
Some parts of this article are sourced from:
thehackernews.com

 Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks
Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks