Cybersecurity professionals have identified still a different malware-as-a-company (MaaS) risk called BunnyLoader which is currently being marketed for sale on the cybercrime underground.
“BunnyLoader delivers several functionalities this kind of as downloading and executing a second-stage payload, thieving browser credentials and procedure information, and much far more,” Zscaler ThreatLabz scientists Niraj Shivtarkar and Satyam Singh mentioned in an examination revealed very last 7 days.
Amongst its other abilities involve working remote commands on the contaminated device, a keylogger to seize keystrokes, and a clipper performance to keep track of the victim’s clipboard and switch material matching cryptocurrency wallet addresses with actor-managed addresses.
A C/C++-based mostly loader offered for $250 for a lifetime license, the malware is claimed to have been underneath continuous development given that its debut on September 4, 2023, with new characteristics and enhancements that incorporate anti-sandbox and antivirus evasion procedures.
Also preset as section of updates unveiled on September 15 and September 27, 2023, are issues with command-and-handle (C2) as very well as “critical” SQL injection flaws in the C2 panel that would have granted accessibility to the database.

A important selling place of BunnyLoader, according to the writer Player_BUNNY (aka Participant_BL), is its fileless loading attribute that “would make it complicated for the antiviruses to take out the attackers malware.”
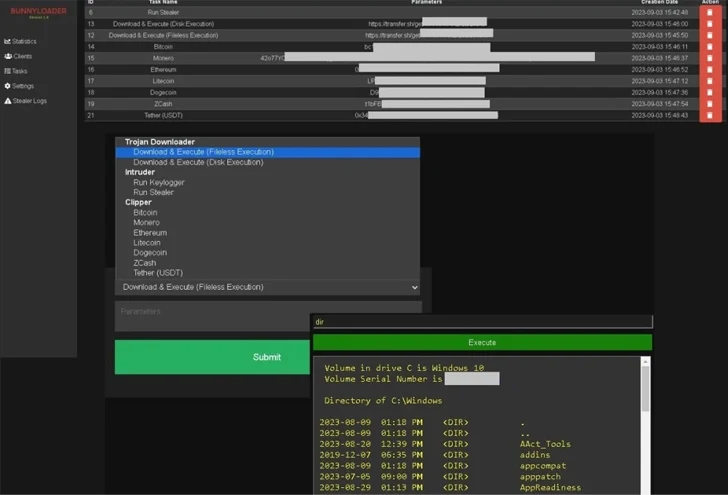
The C2 panel presents options for prospective buyers to watch active jobs, an infection figures, the full number of connected and inactive hosts, and stealer logs. It also offers the means to purge details and remotely regulate the compromised machines.
The exact original entry system made use of to distribute BunnyLoader is at present unclear. The moment set up, the malware sets up persistence through a Windows Registry modify and performs a sequence of sandbox and digital equipment checks in advance of activating its malicious habits by sending job requests to the remote server and fetching the ideal responses.
This features Trojan Downloader tasks to down load and execute up coming-phase malware, Intruder to operate keylogger and stealer for harvesting data from messaging applications, VPN customers, and web browsers, and Clipper to redirect cryptocurrency payments and revenue off illicit transactions.
The final step entails encapsulating all the collected information into a ZIP archive and transmitting it to the server.
“BunnyLoader is a new MaaS risk that is consistently evolving their ways and adding new options to have out prosperous strategies towards their targets,” the scientists mentioned.
The findings comply with the discovery of yet another Windows-dependent loader called MidgeDropper that is probable dispersed via phishing e-mail to deliver an unnamed second-stage payload from a distant server.
The enhancement also arrives amid the debut of two new details stealer malware strains named Agniane Stealer and The-Murk-Stealer that supports the theft of a broad assortment of facts from breached endpoints.

While Agniane Stealer is available as a every month membership for $50, the latter is obtainable on GitHub for allegedly educational functions, building it ripe for abuse by other menace actors. Some of the other stealers hosted on GitHub incorporate Stealerium, Impost3r, Blank-Grabber, Nivistealer, Creal-stealer, and cstealer.
“While boasting the software is for educational purposes, the author’s contradiction occurs when urging not to add the closing binary to platforms like VirusTotal (VT), in which antivirus solutions can detect its signature,” Cyfirma reported.
It is really not just new malware services, as cybercriminals are also augmenting capabilities of existing MaaS platforms with current attack chains to evade detection by security resources. This encompasses a variant of the RedLine Stealer that employs a Windows Batch script to launch the malware.
“[RedLine Stealer] is becoming distributed by many suggests and menace actors are repeatedly earning adjustments to the methods to make it undetectable for an extended period of time of time,” the cybersecurity organization reported. “It is also remaining bought on the underground discussion boards and encouraging cybercriminals to achieve their evil intentions.”
Identified this article intriguing? Stick to us on Twitter and LinkedIn to go through far more exceptional content we submit.
Some parts of this article are sourced from:
thehackernews.com

 Zanubis Android Banking Trojan Poses as Peruvian Government App to Target Users
Zanubis Android Banking Trojan Poses as Peruvian Government App to Target Users