Web Software Security consists of a myriad of security controls that guarantee that a web application:
Web Purposes have turn out to be ubiquitous right after the expansion of Web 2., which Social Media Platforms, E-Commerce web-sites, and email shoppers saturating the internet areas in the latest many years.
As the programs take in and retailer even far more delicate and detailed details, they develop into an at any time a lot more interesting concentrate on for attackers.
Frequent Attack Methods
The a few most typical vulnerabilities that exist in this place are Injections (SQL, Remote Code), Cryptographic Failures (beforehand delicate knowledge exposure), and Damaged Accessibility Management (BAC). Now, we will concentrate on Injections and Damaged Entry Management.
Injections
SQL is the most widespread Database software that is applied, and hosts a plethora of payment details, PII details, and inside company records.
A SQL Injection is an attack that utilizes malicious SQL code for backend database manipulation to obtain information and facts that was not supposed to be displayed.
The setting up place for this, is a command these types of as the a person below:

This will return ALL rows from the “Consumers” table, because OR 1=1 is generally True. Heading even more with this, this system will also return passwords if there are any.
Photo an attack like this currently being executed from a large social media enterprise, or a substantial e-commerce business enterprise, and a single can start off to see how a lot sensitive knowledge can be retrieved with just a person command.
Broken Entry Regulate
Damaged Obtain Regulate (BAC) has risen the ranks on the OWASP best 10 from fifth to the most frequent Web Software Security Hazards. The 34 Typical Weakness Enumerations (CWEs) mapped to Broken Access Regulate experienced far more occurrences in programs than any other category through OWASP’s the latest tests.
The most frequent forms of BAC, is Vertical and Horizontal privilege escalation. Vertical privilege escalation takes place when a person can elevate their privileges and execute actions, they need to not have entry to do.
The CVE-2019-0211, which was an Apache Community Privilege Escalation. This critical vulnerability, from 2019, impacted Apache HTTP servers running on Unix units, especially those making use of the mod_prefork, mod_worker, and mod_party libraries.
This granted attackers the capability to execute unprivileged scripts, likely main to root entry and compromising shared hosting services. Exploiting this flaw needs the manipulation of shared-memory areas in Apache’s employee processes, which have to be finished in advance of initiating an Apache graceful restart.
The beneath is a screenshot of the POC code. As a person can see, a specific level of specialized skill is essential in this respect, on the other hand, vertical privilege escalation can just as very easily come about when a user’s permissions are overly permissive, or not revoked when they go away a organization.
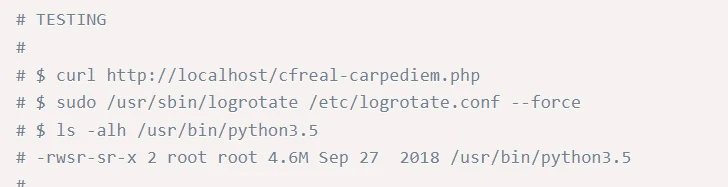
This takes us again to the basic principle of the very least privilege, a ubiquitous term observed throughout the IT world, that is now starting to be extra commonplace as we realise how crucial web programs have become.
Horizontal Privilege Escalation is when a consumer gains access to info they are not intended to have accessibility to, but that knowledge is held at the identical amount as their have permissions. This can be found with just one normal person accessing the info of an additional regular user. Whilst this must not be authorized, the privileges are not soaring vertical, but spreading horizontally. This is in some cases found as additional unsafe, as it can manifest without having boosting any alerts on security methods.
With BAC turning into ever far more existing in the final pair of a long time, it is essential to recall:
- Solely based on obfuscation is not a ample process for access handle.
- If a resource is not meant to be accessible to the public, it must be denied entry by default.
- Builders ought to explicitly specify allowed obtain for just about every resource at the code stage, with entry denial as the default placing.
Very best Tactics – Read through in between the Strains (of code!)
To keep security, developers need to verify incoming knowledge, implement parameterized queries when interacting with databases, and implement successful session administration techniques to defend sensitive details. Considerably of this depends on both the security of web browsers, but also of the back again-end security of the web servers offering web content, top to a segregation of duties in web security.
The most significant trouble that occurs here, is that whilst Web Application Firewalls (WAFs), can mitigate these hazards, a great deal of the responsibility for secure implementation of web information lands at the feet of the builders who put these web sites together. Cybersecurity can normally become an afterthought, with operation currently being chosen.
Realistic Case in point – Enter Validation
Input Validation is the most straightforward and most effective means to implement secure coding, in this example to protect against SQL injections.


In this code, the (user_enter,) is a tuple that contains the user’s input. The database driver will take care of escaping and appropriately handling this input. It guarantees that the input is taken care of as a facts worth, not executable SQL code.
If the person enter has destructive code, these types of as “105 or 1=1,” it is not executed as SQL. In its place, it truly is handled as a worth to be when compared to the UserId in the database.
The database driver immediately handles the escaping of the input, stopping it from impacting the composition of the SQL question or introducing security vulnerabilities.
Web Application Firewalls (WAFs)
A WAF operates at layer 7 of the OSI product, and acts as a reverse proxy, guaranteeing customer visitors passes by the WAF before getting into the backend server. The procedures or insurance policies on the WAF safeguard from the documented vulnerabilities that are existing in these backend servers and filter out destructive traffic.
There are a myriad of WAFs on the current market, and these can all deliver a strong defence from the extra novel assaults, and add properly to a defence in depth tactic, the exercise of secure coding is anything that ensure the foundations of the web application is safe and will not slide victim to extra complicated or novel assaults in the long term.
WAFs are at this time relocating towards a combination of security product that use behavioural-evaluation technologies to detect malicious threats, and even more mitigate towards the threats of extra state-of-the-art ‘bots’ which have been leveraged for reduced-energy attacks on internet websites.
The key downside of working with a WAF, aside from the additional latency and HTTP overhead, is the fact that a WAF can be bypassed by using a -working day exploit towards a web software, which secure coding and correct sanitisation can mitigate towards more successfully that offsetting all Web software security to a WAF. It is critical to recall a WAF is merely a layer of security, and not the overall option.
Incident Reaction and Recovery
SecurityHQ’s strategies to mitigate against attacks:
- This should be coupled with making certain the theory of the very least privilege.
For much more information and facts on these threats, communicate to an qualified here. Or if you suspect a security incident, you can report an incident here.
Observe: This posting was expertly written by Tim Chambers, Senior Cyber Security Supervisor at SecurityHQ
Discovered this article exciting? Abide by us on Twitter and LinkedIn to study far more exceptional information we publish.
Some parts of this article are sourced from:
thehackernews.com


 New Security Vulnerabilities Uncovered in pfSense Firewall Software – Patch Now
New Security Vulnerabilities Uncovered in pfSense Firewall Software – Patch Now