A Brazilian law enforcement operation has led to the arrest of many Brazilian operators in demand of the Grandoreiro malware.
The Federal Police of Brazil reported it served five short term arrest warrants and 13 search and seizure warrants in the states of São Paulo, Santa Catarina, Pará, Goiás, and Mato Grosso.
Slovak cybersecurity business ESET, which furnished extra help in the exertion, mentioned it uncovered a style and design flaw in Grandoreiro’s network protocol that helped it to detect the victimology patterns.
Grandoreiro is a person of the numerous Latin American banking trojans these as Javali, Melcoz, Casabeniero, Mekotio, and Vadokrist, primarily targeting nations like Spain, Mexico, Brazil, and Argentina. It’s recognised to be lively considering that 2017.

In late October 2023, Proofpoint uncovered specifics of a phishing campaign that dispersed an up-to-date model of the malware to targets in Mexico and Spain.
The banking trojan has abilities to equally steal information as a result of keyloggers and screenshots as very well as siphon bank login information and facts from overlays when an contaminated sufferer visits pre-identified banking sites targeted by the risk actors. It can also show faux pop-up windows and block the victim’s screen.
Attack chains ordinarily leverage phishing lures bearing decoy documents or destructive URLs that, when opened or clicked, lead to the deployment of malware, which then establishes speak to with a command-and-command (C&C) server for remotely managing the machine in a handbook style.
“Grandoreiro periodically screens the foreground window to uncover one that belongs to a web browser method,” ESET reported.
“When such a window is uncovered and its title matches any string from a hardcoded record of lender-connected strings, then and only then the malware initiates interaction with its C&C server, sending requests at least when a next right up until terminated.”
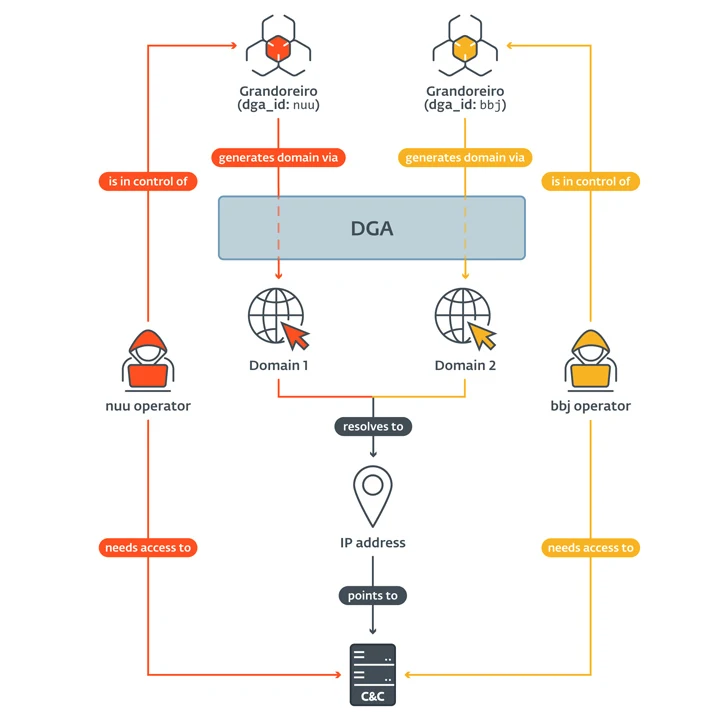
The menace actors at the rear of the malware are also regarded to employ a area era algorithm (DGA) since all over Oct 2020 to dynamically discover a place area for C&C traffic, generating it more durable to block, keep track of, or get in excess of the infrastructure.
A majority of the IP addresses these domains solve to are presented mostly by Amazon Web Expert services (AWS) and Microsoft Azure, with the existence span of the C&C IP addresses ranging any place between 1 day to 425 times. On common, there are 13 lively and three new C&C IP addresses per working day, respectively.

ESET also claimed that Grandoreiro’s flawed implementation of its RealThinClient (RTC) network protocol for C&C manufactured it attainable to get facts about the amount of victims that are linked to the C&C server, which is 551 exceptional victims in a day on common mostly spread across Brazil, Mexico, and Spain.
More investigation has uncovered that an common range of 114 new exclusive victims connect to the C&C servers every single working day.
“The disruption operation led by the Federal Law enforcement of Brazil aimed at people today who are considered to be substantial up in the Grandoreiro operation hierarchy,” ESET said.
Identified this write-up intriguing? Adhere to us on Twitter and LinkedIn to browse a lot more exceptional content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 URGENT: Upgrade GitLab – Critical Workspace Creation Flaw Allows File Overwrite
URGENT: Upgrade GitLab – Critical Workspace Creation Flaw Allows File Overwrite