An ongoing social engineering marketing campaign is focusing on computer software builders with bogus npm offers beneath the guise of a work interview to trick them into downloading a Python backdoor.
Cybersecurity agency Securonix is tracking the activity less than the identify DEV#POPPER, linking it to North Korean menace actors.
“All through these fraudulent interviews, the developers are frequently asked to perform tasks that entail downloading and working software package from resources that appear respectable, these types of as GitHub,” security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov claimed. “The program contained a destructive Node JS payload that, after executed, compromised the developer’s procedure.”

Information of the marketing campaign 1st emerged in late November 2023, when Palo Alto Networks Unit 42 detailed an exercise cluster dubbed Contagious Job interview in which the menace actors pose as employers to lure computer software builders into putting in malware such as BeaverTail and InvisibleFerret by means of the job interview procedure.
Then earlier this February, application supply chain security company Phylum uncovered a set of destructive offers on the npm registry that shipped the very same malware households to siphon sensitive information from compromised developer systems.
It really is worth noting that Contagious Job interview is reported to be disparate from Operation Desire Work (aka DeathNote or NukeSped), with Device 42 telling The Hacker Information that the previous is “targeted on targeting developers, predominantly by pretend identities in freelance position portals, and the next levels require the use of developer instruments and npm deals foremost to […] BeaverTail and InvisibleFerret.”
Procedure Desire Career, linked to the prolific Lazarus Team from North Korea, is a extended-working offensive campaign that sends unsuspecting professionals used in different sectors like aerospace, cryptocurrency, protection, and other sectors malicious documents dressed as position presents to distribute malware.
1st uncovered by Israeli cybersecurity agency ClearSky at the begin of 2020, it also exhibits overlaps with two other Lazarus clusters regarded as Operation In(ter)ception and Procedure North Star.
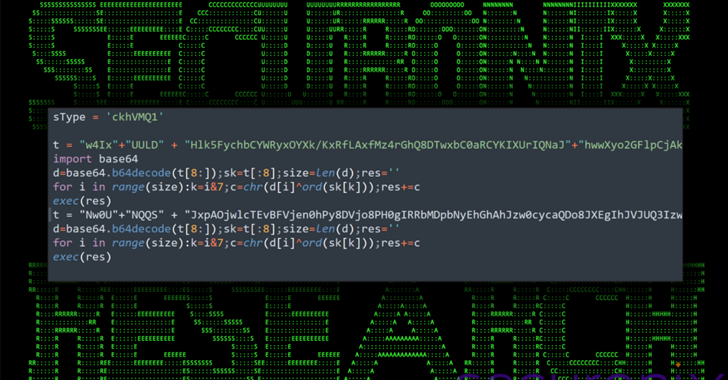
The attack chain detailed by Securonix begins with a ZIP archive hosted on GitHub that’s possible despatched to the concentrate on as component of the job interview. Existing in the file is a seemingly innocuous npm module that harbors a malicious JavaScript file codenamed BeaverTail that functions as an information and facts stealer and a loader for a Python backdoor named InvisibleFerret which is retrieved from a remote server.

The implant, in addition to gathering procedure data, is capable of command execution, file enumeration and exfiltration, and clipboard and keystroke logging.
The enhancement is a sign that North Korean risk actors continue to hone a raft of weapons for their cyber attack arsenal, continually updating their tradecraft with enhanced talents to disguise their steps and blend in on host systems and networks, not to point out siphon off details and flip compromises into economical obtain.
“When it will come to assaults which originate through social engineering, it is really critical to retain a security-concentrated mentality, specifically for the duration of rigorous and annoying circumstances like job interviews,” Securonix scientists mentioned.
“The attackers driving the DEV#POPPER campaigns abuse this, figuring out that the person on the other conclude is in a highly distracted and in a a great deal extra vulnerable point out.”
Located this posting intriguing? Comply with us on Twitter and LinkedIn to read additional unique content material we publish.
Some parts of this article are sourced from:
thehackernews.com

 Severe Flaws Disclosed in Brocade SANnav SAN Management Software
Severe Flaws Disclosed in Brocade SANnav SAN Management Software