Ransomware attacks are a main problem for organizations everywhere you go, and the severity of this issue carries on to intensify.
Just lately, Microsoft’s Incident Reaction crew investigated the BlackByte 2. ransomware assaults and uncovered these cyber strikes’ terrifying velocity and detrimental nature.
The conclusions suggest that hackers can full the full attack system, from getting preliminary entry to producing major damage, in just 5 days. They squander no time infiltrating systems, encrypting vital info, and demanding a ransom to release it.
This shortened timeline poses a significant obstacle for businesses striving to protect on their own against these damaging operations.
BlackByte ransomware is applied in the last phase of the attack, using an 8-digit amount important to encrypt the facts.
To carry out these attacks, hackers use a impressive combination of instruments and methods. The investigation disclosed that they acquire edge of unpatched Microsoft Trade Servers—an method that has verified highly effective. By exploiting this vulnerability, they obtain initial entry to the focus on networks and set the phase for their destructive activities.
The ransomware even further employs process hollowing and antivirus evasion approaches to guarantee productive encryption and circumvent detection.
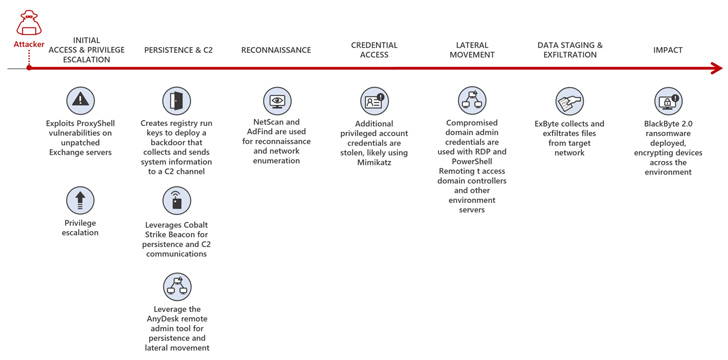
On top of that, web shells equip them with distant entry and management, enabling them to preserve a presence in the compromised methods.
The report also highlighted the deployment of Cobalt Strike beacons, which aid command and command functions. These innovative instruments give attackers a vast range of techniques, earning it far more difficult for businesses to protect from them.
Impending WEBINAR🔐 Privileged Access Management: Understand How to Conquer Vital Problems
Explore distinct approaches to conquer Privileged Account Administration (PAM) troubles and degree up your privileged access security strategy.
Reserve Your Location
Alongside these techniques, the investigation uncovered numerous other troubling procedures cybercriminals use. They benefit from “living-off-the-land” equipment to mix in with authentic processes and escape detection.
The ransomware modifies quantity shadow copies on contaminated machines to protect against knowledge restoration by means of method restore details. The attackers also deploy specially-crafted backdoors, ensuring continued accessibility for the attackers even just after the initial compromise.
The disturbing upsurge in ransomware attacks demands speedy motion from organizations all over the world. In reaction to these conclusions, Microsoft has supplied some realistic suggestions.
Organizations are mostly urged to carry out sturdy patch management methods, ensuring they well timed utilize critical security updates. Enabling tamper defense is another important move, as it strengthens security solutions versus malicious attempts to disable or bypass them.
Uncovered this write-up fascinating? Abide by us on Twitter and LinkedIn to read through additional unique information we article.
Some parts of this article are sourced from:
thehackernews.com


 Google Releases Android Patch Update for 3 Actively Exploited Vulnerabilities
Google Releases Android Patch Update for 3 Actively Exploited Vulnerabilities