Cybersecurity scientists have uncovered a privilege escalation vulnerability in Google Cloud that could allow malicious actors tamper with application illustrations or photos and infect people, top to source chain attacks.
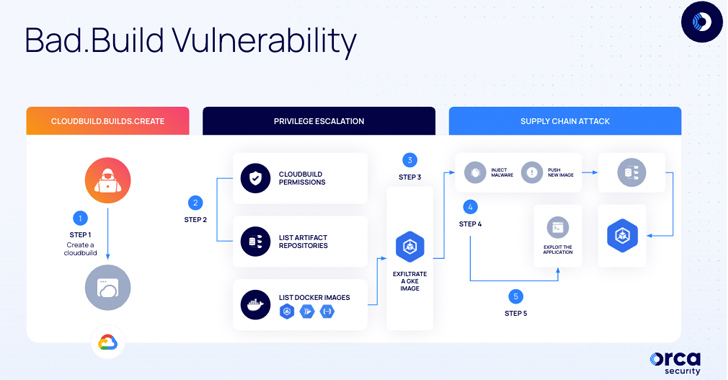
The issue, dubbed Poor.Create, is rooted in the Google Cloud Establish company, in accordance to cloud security business Orca, which identified and claimed the issue.
“By abusing the flaw and enabling an impersonation of the default Cloud Construct provider, attackers can manipulate images in the Google Artifact Registry and inject destructive code,” the firm said in a statement shared with The Hacker Information.
“Any purposes developed from the manipulated images are then impacted and, if the malformed apps are meant to be deployed on customer’s environments, the risk crosses from the giving organization’s surroundings to their customers’ environments, constituting a significant provide chain risk.”
Subsequent accountable disclosure, Google has issued a partial correct that won’t eliminate the privilege escalation vector, describing it as a lower-severity issue. No even further purchaser motion is necessary.
The layout flaw stems from the fact that Cloud Create instantly generates a default provider account to execute builds for a project on users’ behalf. Particularly, the company account arrives with excessive permissions (“logging.privateLogEntries.checklist”), which lets entry to audit logs made up of the complete record of all permissions on the venture.
“What would make this facts so beneficial is that it significantly facilitates lateral motion and privilege escalation in the atmosphere,” Orca researcher Roi Nisimi stated. “Realizing which GCP account can carry out which motion, is equal to fixing a wonderful piece of the puzzle on how to start an attack.”
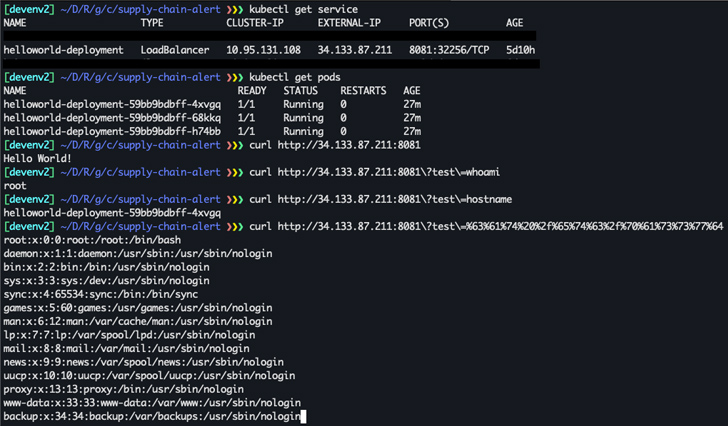
In executing so, a malicious actor could abuse the “cloudbuild.builds.make” authorization previously obtained by other means to impersonate the Google Cloud Develop assistance account and acquire elevated privileges, exfiltrate an impression that is getting made use of within Google Kubernetes Motor (GKE), and alter it to integrate malware.
“After the destructive graphic is deployed, the attacker can exploit it and run code on the docker container as root,” Nisimi stated.
Approaching WEBINARShield Towards Insider Threats: Grasp SaaS Security Posture Management
Anxious about insider threats? We’ve obtained you lined! Join this webinar to investigate useful approaches and the secrets and techniques of proactive security with SaaS Security Posture Management.
Be a part of Nowadays
The patch place in spot by Google revokes the logging.privateLogEntries.listing authorization from the Cloud Construct assistance account, thereby blocking accessibility to enumerate personal logs by default.
This is not the first time privilege escalation flaws impacting the Google Cloud System have been described. In 2020, Gitlab, Rhino Security Labs, and Praetorian thorough various strategies that could be exploited to compromise cloud environments.
Buyers are suggested to observe the habits of the default Google Cloud Make service account to detect any possible malicious actions as properly as use the theory of least privilege (PoLP) to mitigate doable risks.
Identified this short article exciting? Observe us on Twitter and LinkedIn to examine additional exclusive written content we article.
Some parts of this article are sourced from:
thehackernews.com

 U.S. Government Blacklists Cytrox and Intellexa Spyware Vendors for Cyber Espionage
U.S. Government Blacklists Cytrox and Intellexa Spyware Vendors for Cyber Espionage