A number of danger actors have capitalized on the leak of Babuk (aka Babak or Babyk) ransomware code in September 2021 to establish as a lot of as nine various ransomware people capable of focusing on VMware ESXi systems.
“These variants emerged through H2 2022 and H1 2023, which shows an expanding development of Babuk resource code adoption,” SentinelOne security researcher Alex Delamotte reported in a report shared with The Hacker News.
“Leaked resource code allows actors to concentrate on Linux devices when they may perhaps in any other case lack expertise to establish a operating system.”
A selection of cybercrime teams, both of those massive and small, have established their sights on ESXi hypervisors. What is much more, at the very least three different ransomware strains – Cylance, Rorschach (aka BabLock), RTM Locker – that have emerged given that the begin of the yr are centered on the leaked Babuk source code.

SentinelOne’s most up-to-date evaluation displays that this phenomenon is much more typical, with the cybersecurity corporation determining source code overlaps in between Babuk and ESXi lockers attributed to Conti and REvil (aka REvix).
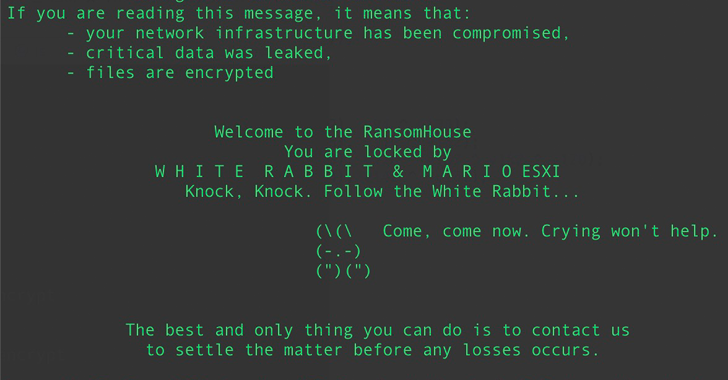
Other ransomware families that have ported various capabilities from Babuk into their respective code contain LOCK4, DATAF, Mario, Play, and Babuk 2023 (aka XVGV) ransomware.
In spite of this obvious craze, SentinelOne said it observed no parallels concerning Babuk and ALPHV, Black Basta, Hive, and LockBit’s ESXi lockers, adding it discovered “minimal similarity” involving ESXiArgs and Babuk, indicating an erroneous attribution.
“Based mostly on the popularity of Babuk’s ESXi locker code, actors could also convert to the group’ Go-centered NAS locker,” Delamotte mentioned. “Golang continues to be a area of interest choice for many actors, but it continues to maximize in attractiveness.”
Upcoming WEBINARLearn to Cease Ransomware with Serious-Time Safety
Join our webinar and find out how to prevent ransomware attacks in their tracks with real-time MFA and provider account security.
Conserve My Seat!
The improvement comes as threat actors associated with Royal ransomware, who are suspected to be previous Conti associates, have expanded their attack toolkit with an ELF variant that is capable of striking Linux and ESXi environments.
“The ELF variant is fairly very similar to the Windows variant, and the sample does not incorporate any obfuscation,” Palo Alto Networks Unit 42 explained in a produce-up revealed this week. “All strings, which includes the RSA community crucial and ransom observe, are saved as plaintext.”
Royal ransomware assaults are facilitated by usually means of many initial obtain vectors this sort of as callback phishing, BATLOADER infections, or compromised credentials, which is then abused to drop a Cobalt Strike Beacon as a precursor to ransomware execution.
Considering the fact that bursting on the scene in September 2022, Royal ransomware has claimed accountability for concentrating on 157 organizations on their leak web-site, with most of the attacks focusing on manufacturing, retail, legal expert services, training, building, and healthcare providers in the U.S., Canada, and Germany.
Identified this article intriguing? Observe us on Twitter and LinkedIn to study additional special articles we publish.
Some parts of this article are sourced from:
thehackernews.com

 Ransomware Group Tries and Fails to Extort Security Vendor Dragos
Ransomware Group Tries and Fails to Extort Security Vendor Dragos