Microsoft is warning about the likely abuse of Azure Company Tags by malicious actors to forge requests from a trusted assistance and get about firewall procedures, thus letting them to achieve unauthorized access to cloud sources.
“This case does spotlight an inherent risk in utilizing assistance tags as a single mechanism for vetting incoming network site visitors,” the Microsoft Security Reaction Heart (MSRC) mentioned in a guidance issued very last week.
“Provider tags are not to be dealt with as a security boundary and really should only be employed as a routing mechanism in conjunction with validation controls. Support tags are not a thorough way to safe visitors to a customer’s origin and do not change input validation to avert vulnerabilities that might be connected with web requests.”
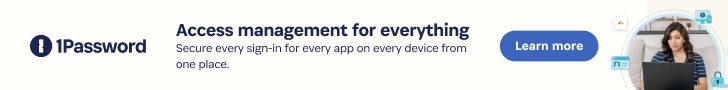
The statement will come in response to conclusions from cybersecurity agency Tenable, which located that Azure shoppers whose firewall rules count on Azure Assistance Tags could be bypassed. There is no evidence that the characteristic has been exploited in the wild.
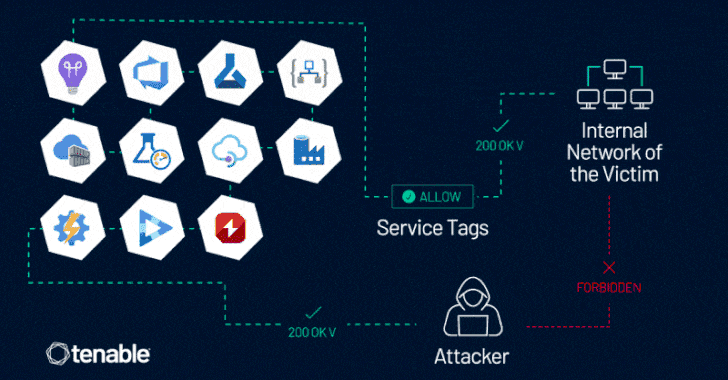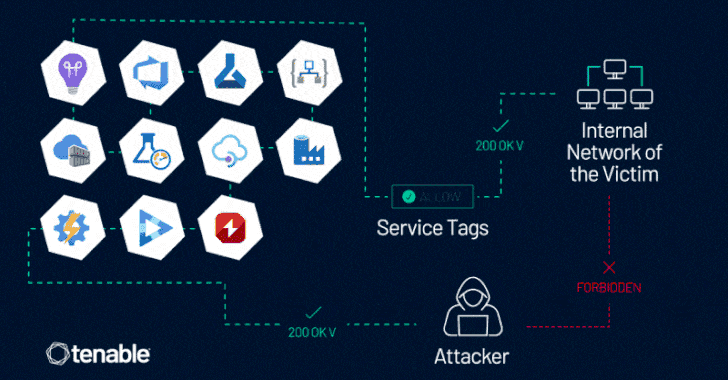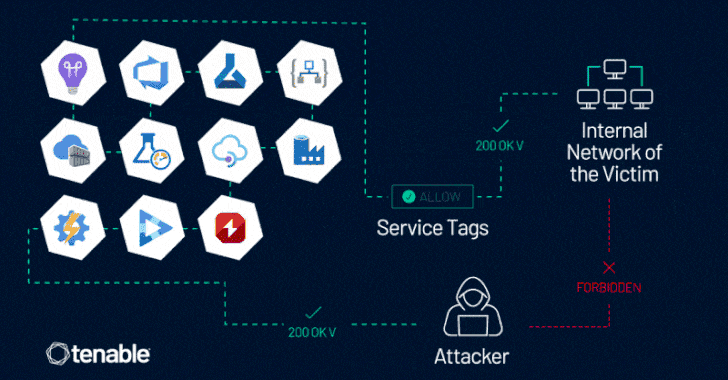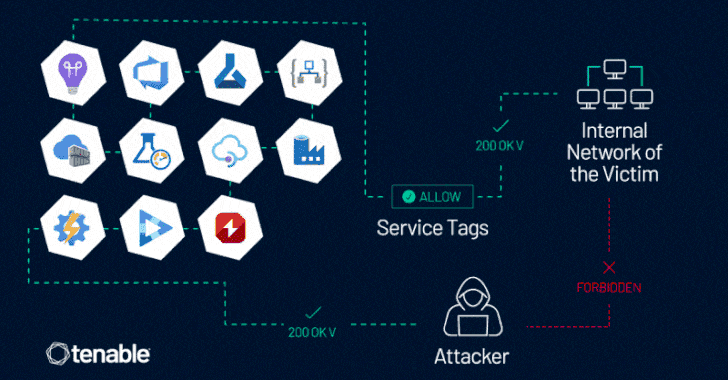
The challenge, at its main, stems from the truth that some of the Azure providers enable inbound website traffic by using a provider tag, probably enabling an attacker in 1 tenant to send out specifically crafted web requests to accessibility assets in yet another, assuming it has been configured to allow for website traffic from the provider tag and does not conduct any authentication of its very own.
At 10 Azure products and services have been discovered susceptible: Azure Application Insights, Azure DevOps, Azure Device Mastering, Azure Logic Apps, Azure Container Registry, Azure Load Testing, Azure API Management, Azure Details Manufacturing unit, Azure Action Group, Azure AI Video Indexer, and Azure Chaos Studio.
“This vulnerability enables an attacker to control server-facet requests, as a result impersonating reliable Azure products and services,” Tenable researcher Liv Matan said. “This enables the attacker to bypass network controls based mostly on Assistance Tags, which are typically used to protect against community entry to Azure customers’ inner property, knowledge, and providers.”
In response to the disclosure in late January 2024, Microsoft has current the documentation to explicitly notice that “Support Tags alone usually are not ample to protected traffic without the need of taking into consideration the mother nature of the support and the targeted traffic it sends.”
It really is also suggested that customers assessment their use of service tags and make sure they have adopted satisfactory security guardrails to authenticate only dependable network visitors for company tags.
Found this article appealing? Follow us on Twitter and LinkedIn to read through far more unique articles we post.
Some parts of this article are sourced from:
thehackernews.com

 Google Takes Down Influence Campaigns Tied to China, Indonesia, and Russia
Google Takes Down Influence Campaigns Tied to China, Indonesia, and Russia