New cybersecurity investigate has located that command-line interface (CLI) resources from Amazon Web Solutions (AWS) and Google Cloud can expose delicate credentials in construct logs, posing important hazards to organizations.
The vulnerability has been codenamed LeakyCLI by cloud security organization Orca.
“Some commands on Azure CLI, AWS CLI, and Google Cloud CLI can expose sensitive info in the type of surroundings variables, which can be gathered by adversaries when released by instruments these types of as GitHub Steps,” security researcher Roi Nisimi explained in a report shared with The Hacker News.
Microsoft has considering that dealt with the issue as element of security updates produced in November 2023, assigned it the CVE identifier CVE-2023-36052 (CVSS score: 8.6).

The notion, in a nutshell, has to do with how the CLI instructions these kinds of as could be applied to show (pre-)defined atmosphere variables and output to Ongoing Integration and Continual Deployment (CI/CD) logs. A listing of these types of commands spanning AWS and Google Cloud is down below
- aws lambda get-purpose-configuration
- aws lambda get-function
- aws lambda update-operate-configuration
- aws lambda update-functionality-code
- aws lambda publish-edition
- gcloud capabilities deploy
–established-env-vars - gcloud capabilities deploy
–update-env-vars - gcloud functions deploy
–take out-env-vars
Orca mentioned it identified several assignments on GitHub that inadvertently leaked accessibility tokens and other delicate info through Github Actions, CircleCI, TravisCI, and Cloud Build logs.
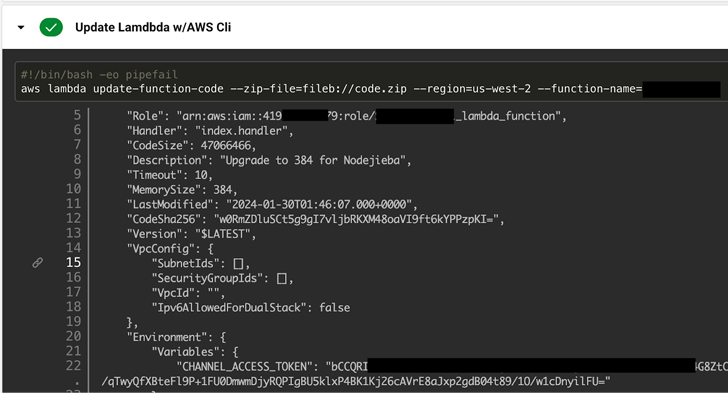
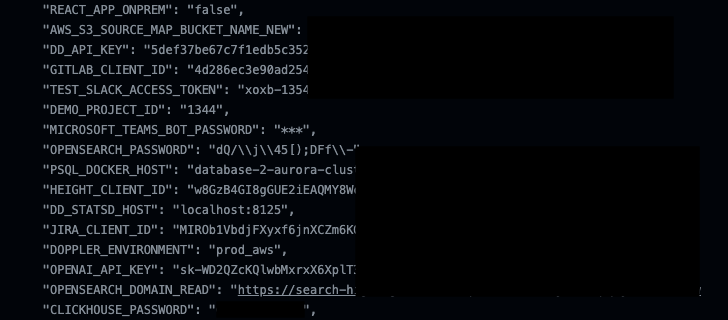
In contrast to Microsoft, on the other hand, both equally Amazon and Google look at this to be anticipated behavior, requiring that corporations acquire actions to keep away from storing techniques in environment variables and as an alternative use a devoted secrets shop company like AWS Techniques Supervisor or Google Cloud Secret Manager.

Google also suggests the use of the “–no-user-output-enabled” option to suppress the printing of command output to normal output and standard mistake in the terminal.
“If poor actors get their hands on these atmosphere variables, this could likely guide to look at sensitive info like qualifications, these types of as passwords, person names, and keys, which could permit them to access any resources that the repository proprietors can,” Nisimi mentioned.
“CLI commands are by default assumed to be operating in a protected atmosphere, but coupled with CI/CD pipelines, they may pose a security risk.”
Found this article attention-grabbing? Follow us on Twitter and LinkedIn to go through extra distinctive content material we publish.
Some parts of this article are sourced from:
thehackernews.com


 Widely-Used PuTTY SSH Client Found Vulnerable to Key Recovery Attack
Widely-Used PuTTY SSH Client Found Vulnerable to Key Recovery Attack