Staff offboarding is no one’s beloved process, nevertheless it is a critical IT process that wants to be executed diligently and effectively. That is less difficult mentioned than carried out, specifically considering that IT organizations have considerably less visibility and manage more than employees’ IT use than ever. Now, workers can quickly undertake new cloud and SaaS programs any time and anywhere they want, and the aged IT offboarding playbook of “disable Advert account, forward email, recuperate and wipe unit, and connect with it a day” is no for a longer time more than enough.
Listed here, we are going to cover five of the most typical pitfalls of IT offboarding in a SaaS-first entire world, alongside with advice on how to navigate all over them.
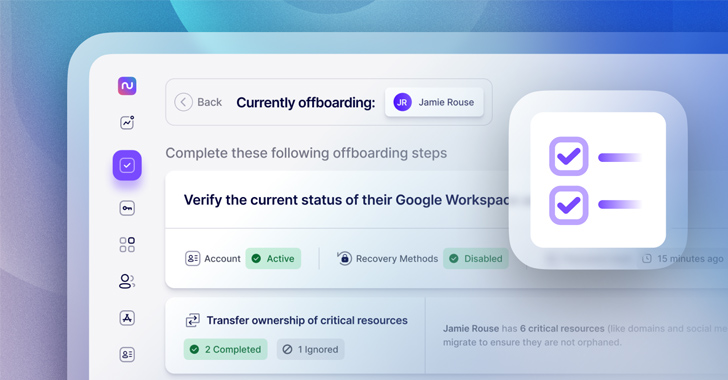
Pitfall #1: Suspending or deleting the email account ahead of finishing other critical methods
It may well feel sensible to suspend or delete the employees’ Google Workspace or Microsoft 365 account as the very first step in the offboarding process. However, this will make the account inaccessible to anyone, even admins, which could interfere with your means to entire other offboarding jobs like transferring documents and details.
As a substitute of suspending or deleting the account, you may want to revoke the previous employee’s obtain to their email account by resetting their passwords and turning off any restoration methods the worker experienced established up, these as a secondary personalized email deal with or cellular quantity.
Pinpointing when to suspend or delete the employees’ email account will rely on inside protocol, and ought to be meticulously completed only after confirming that access to all other critical assets, systems and info have been revoked or transferred to other staff members. Commonly, this will be the ultimate action in the IT offboarding system.
Pitfall #2: Contemplating only what is in IdP or SSO
A person of the most widespread offboarding pitfalls is restricting the scope to only the sanctioned cloud and SaaS applications that are managed in your identification company (IdP) or organization one indicator-on method (SSO.) When it looks reasonable to design an offboarding course of action with a one id destroy-change, the fact we all stay with is that not almost everything is powering SSO, and by narrowing your scope, you risk overlooking all of the unsanctioned or “shadow” SaaS belongings an worker launched in the course of their tenure. This sort of unsanctioned SaaS accounts are often produced with a username and password, which can easily wander out the doorway on a Article-it note or be still left deserted and later compromised by a danger actor. To keep away from this pitfall, get started by opening the aperture of your IT offboarding to encompass all managed and unmanaged cloud and SaaS access.
So, how do you build a list of the unmanaged cloud and SaaS accounts for a departing staff? This can turn into the world’s worst scavenger hunt, with you obtaining to cross-reference information from finance units, your assistance desk ticketing platform, inquiries to application proprietors outside of IT, teammates of the departing staff, and much more.
But don’t embark on that hunt yet, new answers for SaaS management are rising to make this approach a whole whole lot less difficult.
Pitfall #3: Overlooking company-critical cloud and SaaS methods
It is effortless to ignore to transfer the possession of critical resources like company social media accounts, root account possession, and registered domains. This slip-up can direct to organization disruption or leave accounts orphaned and inaccessible. To be certain this isn’t going to occur, IT organizations should be guaranteed to identify and transfer ownership of any small business-critical methods, automations, or integrations as an early stage of the offboarding approach.
Pitfall #4: Not involving the small business homeowners of every single SaaS software
The immediate increase of organization-led IT signifies that more IT administration is happening outdoors of central IT. This means additional people to engage in the offboarding course of action, which includes software enterprise proprietors and business enterprise technologists who regulate the budgets and licenses for their SaaS apps.
There are two essential methods to simplifying this course of action: initial, you have to know who the proper people are to engage, which demands a robust SaaS administration platform. 2nd, you need to have a way to streamline and even automate engagement with all stakeholders in buy to proficiently orchestrate the multitude of offboarding jobs that non-IT directors should complete.
For instance, prior to the departing employee’s account within just a distinct app is shut down, the application business enterprise operator may need to have to transfer ownership of details, integrations, or workflows to keep away from disrupting the small business. Additionally, the application operator may well need to transfer any elevated permissions to a new user.
Pitfall #5: Overlooking app-to-application OAuth integrations
In most organizations these days,a web of application-to-application OAuth integrations exists in get to automate data updates and tasks throughout apps. When staff members depart the firm, revoking grants devoid of thorough review could guide to enterprise disruption, and not revoking grants could lead to improved risk.
As a result, it can be critical to evaluate OAuth grants, operate with software homeowners to detect any that will need to be reinstated via a diverse account, and then revoke the grants issued by the departing employee’s accounts.
Automate SaaS offboarding with Nudge Security
IT offboarding is monotonous, time-consuming and often incomplete. But, Nudge Security can make this approach much less difficult.
Nudge Security continually discovers and inventories all the SaaS and cloud apps your staff members are employing, like shadow IT, offering you a solitary source of fact for a departing users’ accounts, OAuth grants, and other critical methods. And, the crafted-in offboarding playbook automates up to 90% of manual jobs like resetting passwords, revoking OAuth grants, messaging application owners to transfer information and permissions, and far more.
See how you can automate IT offboarding with Nudge Security.
Observed this posting interesting? Comply with us on Twitter and LinkedIn to examine extra exclusive information we publish.
Some parts of this article are sourced from:
thehackernews.com

 N-Able’s Take Control Agent Vulnerability Exposes Windows Systems
N-Able’s Take Control Agent Vulnerability Exposes Windows Systems