The risk actor regarded as Asylum Ambuscade has been observed straddling cybercrime and cyber espionage functions due to the fact at minimum early 2020.
“It is a crimeware team that targets financial institution prospects and cryptocurrency traders in different locations, which includes North America and Europe,” ESET said in an analysis revealed Thursday. “Asylum Ambuscade also does espionage towards authorities entities in Europe and Central Asia.”
Asylum Ambuscade was to start with documented by Proofpoint in March 2022 as a nation-condition-sponsored phishing marketing campaign that targeted European governmental entities in an endeavor to get intelligence on refugee and supply movement in the area.
The intention of the attackers, per the Slovak cybersecurity business, is to siphon confidential data and web email qualifications from formal federal government email portals.

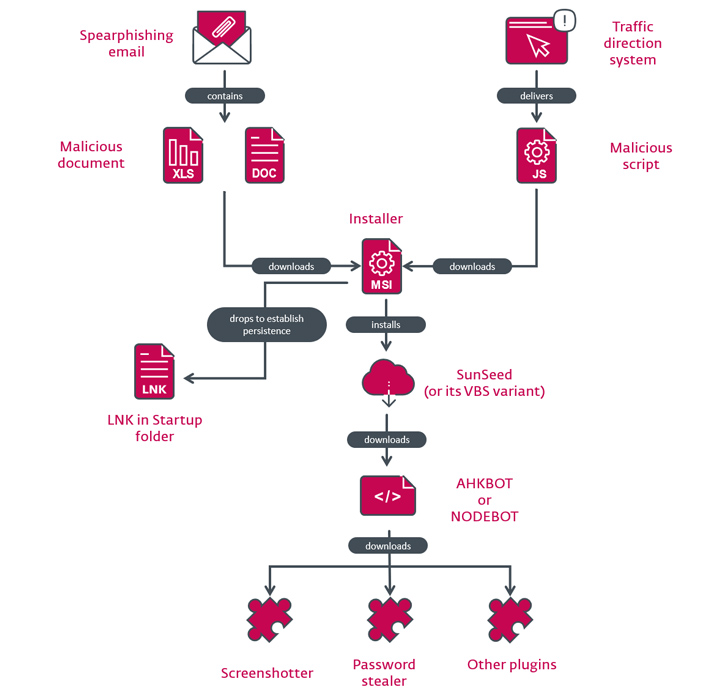
The assaults commence off with a spear-phishing email bearing a destructive Excel spreadsheet attachment that, when opened, either exploits VBA code or the Follina vulnerability (CVE-2022-30190) to down load an MSI package deal from a distant server.
The installer, for its part, deploys a downloader written in Lua known as SunSeed (or its Visual Simple Script equal) that, in transform, retrieves an AutoHotkey-primarily based malware recognised as AHK Bot from a distant server.
What is actually noteworthy about Asylum Ambuscade is its cybercrime spree that has claimed around 4,500 victims throughout the environment considering the fact that January 2022, with a majority of them located in North The usa, Asia, Africa, Europe, and South The usa.
“The targeting is quite huge and typically incorporates individuals, cryptocurrency traders, and little and medium enterprises (SMBs) in several verticals,” ESET researcher Matthieu Faou reported.
Whilst 1 component of the attacks is created to steal cryptocurrency, the targeting of SMBs is probable an try to monetize the accessibility by selling it to other cybercriminal teams for illicit gains.
The compromise chain follows a comparable sample barring the original intrusion vector, which involves the use of a rogue Google Ad or a website traffic direction program (TDS) to redirect probable victims to a bogus web page delivering a malware-laced JavaScript file.
Impending WEBINAR🔐 Mastering API Security: Understanding Your Real Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive techniques toward ironclad security. Sign up for our insightful webinar!
Be a part of the Session.wn-button,.wn-label,.wn-label:right afterdisplay:inline-block.check_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-suitable-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-body weight:600letter-spacing:.6pxcolor:#596cec.wn-label:soon afterwidth:50pxheight:6pxcontent:”border-top rated:2px reliable #d9deffmargin: 8px.wn-titlefont-measurement:21pxpadding:10px 0font-excess weight:900textual content-align:leftline-peak:33px.wn-descriptiontextual content-align:leftfont-dimension:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-color:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-weight:500letter-spacing:.2px
The attacks have also made use of a Node.js variation of AHK Bot codenamed NODEBOT which is then employed to obtain plugins liable for getting screenshots, plundering passwords, collecting program information and facts, and setting up extra trojans and stealers.
Specified the almost similar attack chains across cybercrime and espionage efforts, it truly is suspected that “Asylum Ambuscade is a cybercrime group that is performing some cyber espionage on the facet.”
The overlaps also increase to an additional exercise cluster dubbed Screentime that is identified to concentrate on corporations in the U.S. and Germany with bespoke malware created to steal confidential facts. Proofpoint is monitoring the menace actor less than the title TA866.
“It is pretty strange to capture a cybercrime team jogging devoted cyberespionage operations,” Faou explained, generating it fairly of a rarity in the danger landscape.
Discovered this report interesting? Follow us on Twitter and LinkedIn to browse much more exceptional information we publish.
Some parts of this article are sourced from:
thehackernews.com


 Google Launches Framework to Secure Generative AI
Google Launches Framework to Secure Generative AI