The Russia-joined danger actor recognised as APT28 has been connected to many ongoing phishing campaigns that make use of lure paperwork imitating governing administration and non-governmental organizations (NGOs) in Europe, the South Caucasus, Central Asia, and North and South The usa.
“The uncovered lures involve a combination of inner and publicly out there documents, as very well as doable actor-produced paperwork affiliated with finance, critical infrastructure, govt engagements, cyber security, maritime security, health care, enterprise, and defense industrial output,” IBM X-Pressure reported in a report revealed previous 7 days.
The tech enterprise is monitoring the action below the moniker ITG05, which is also identified as Blue Athena, BlueDelta, Extravagant Bear, Fighting Ursa, Forest Blizzard (previously Strontium), FROZENLAKE, Iron Twilight, Pawn Storm, Sednit, Sofacy, TA422, and UAC-028.

The disclosure will come much more than a few months right after the adversary was noticed applying decoys connected to the ongoing Israel-Hamas war to provide a custom backdoor dubbed HeadLace.
APT28 has due to the fact also qualified Ukrainian governing administration entities and Polish corporations with phishing messages designed to deploy bespoke implants and details stealers like MASEPIE, OCEANMAP, and STEELHOOK.
Other campaigns have entailed the exploitation of security flaws in Microsoft Outlook (CVE-2023-23397, CVSS rating: 9.8) to plunder NT LAN Manager (NTLM) v2 hashes, boosting the possibility that the danger actor may perhaps leverage other weaknesses to exfiltrate NTLMv2 hashes for use in relay attacks.
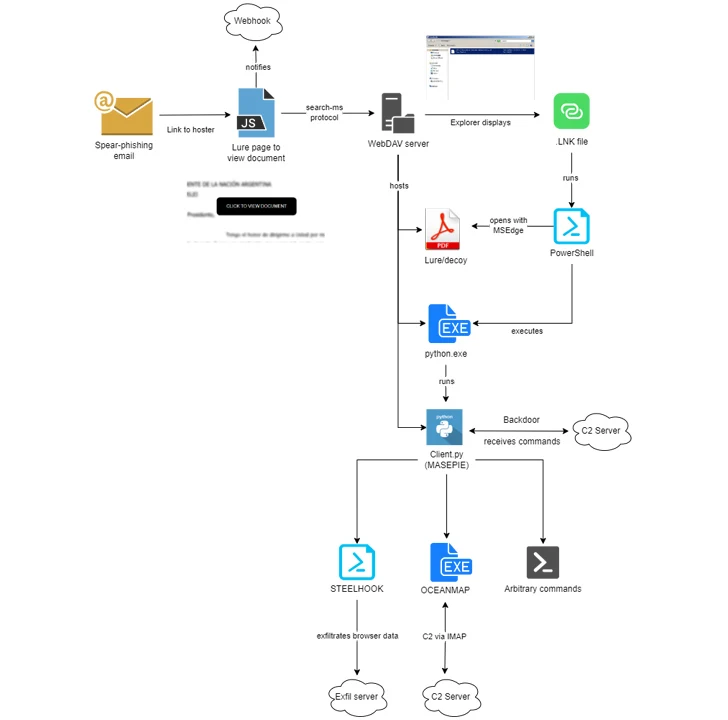
The most up-to-date strategies noticed by IBM X-Drive involving late November 2023 and February 2024 leverage the “lookup-ms:” URI protocol handler in Microsoft Windows to trick victims into downloading malware hosted on actor-managed WebDAV servers.
There is evidence to recommend that both equally the WebDAV servers, as nicely as the MASEPIE C2 servers, may be hosted on compromised Ubiquiti routers, a botnet comprising which was taken down by the U.S. governing administration very last thirty day period.

The phishing attacks impersonate entities from many countries this sort of as Argentina, Ukraine, Ga, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the U.S., placing to use a combine of reliable publicly available authorities and non-federal government lure files to activate the infection chains.
“In an update to their methodologies, ITG05 is employing the freely obtainable hosting company, firstcloudit[.]com to stage payloads to allow ongoing operations,” security researchers Joe Fasulo, Claire Zaboeva, and Golo Mühr mentioned.
The climax of APT28’s elaborate plan finishes with the execution of MASEPIE, OCEANMAP, and STEELHOOK, which are created to exfiltrate files, operate arbitrary commands, and steal browser details. OCEANMAP has been characterized as a additional capable model of CredoMap, an additional backdoor earlier discovered as made use of by the group.
“ITG05 continues to be adaptable to modifications in opportunity by offering new an infection methodologies and leveraging commercially readily available infrastructure, even though regularly evolving malware abilities,” the researchers concluded.
Found this report interesting? Abide by us on Twitter and LinkedIn to read through extra exclusive material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Hackers Using Cracked Software on GitHub to Spread RisePro Info Stealer
Hackers Using Cracked Software on GitHub to Spread RisePro Info Stealer