A new Android malware marketing campaign has been noticed pushing the Anatsa banking trojan to target banking consumers in the U.S., U.K., Germany, Austria, and Switzerland given that the get started of March 2023.
“The actors behind Anatsa goal to steal credentials made use of to authorize customers in cell banking programs and execute Unit-Takeover Fraud (DTO) to initiate fraudulent transactions,” ThreatFabric stated in an evaluation released Monday.
The Dutch cybersecurity corporation mentioned Anatsa-infected Google Play Keep dropper applications have accrued around 30,000 installations to day, indicating that the official application storefront has come to be an productive distribution vector for the malware.

Anatsa, also recognized by the title TeaBot and Toddler, 1st emerged in early 2021, and has been observed masquerading as seemingly innocuous utility applications like PDF audience, QR code scanners, and two-factor authentication (2FA) apps on Google Enjoy to siphon users’ credentials. It has considering the fact that come to be a single of the most prolific banking malware, focusing on around 400 economic establishments throughout the environment.
The trojan characteristics backdoor-like abilities to steal info and also performs overlay attacks in get to steal qualifications as properly as log functions by abusing its permissions to Android’s accessibility providers API. It can additional bypass existing fraud handle mechanisms to carry out unauthorized fund transfers.

“Because transactions are initiated from the exact product that specific lender clients frequently use, it has been noted that it is extremely complicated for banking anti-fraud systems to detect it,” ThreatFabric pointed out.
In the most up-to-date campaign noticed by ThreatFabric, the dropper app, after put in, can make a ask for to a GitHub site that details to yet another GitHub URL hosting the destructive payload, which aims to trick victims by disguising them selves as app incorporate-ons. It is suspected that consumers are routed to these applications through sketchy adverts.
A notable aspect of the dropper is its use of the limited “Request_Put in_Offers” authorization, which has been continuously exploited by rogue apps dispersed by means of the Google Participate in Store to set up extra malware on the infected unit. The names of the applications are as follows –
- All Document Reader & Editor (com.mikijaki.documents.pdfreader.xlsx.csv.ppt.docs)
- All Document Reader and Viewer (com.muchlensoka.pdfcreator)
- PDF Reader – Edit & Perspective PDF (lsstudio.pdfreader.powerfultool.allinonepdf.goodpdftools)
- PDF Reader & Editor (com.proderstarler.pdfsignature)
- PDF Reader & Editor (moh.filemanagerrespdf)
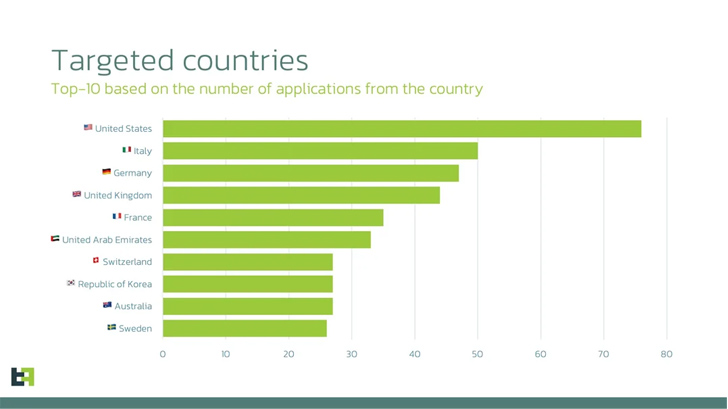
The list of leading nations around the world that are of interest to Anatsa based mostly on the variety of financial applications specific incorporate the U.S., Italy, Germany, the U.K., France, the U.A.E., Switzerland, South Korea, Australia, and Sweden. Also present in the list are Finland, Singapore, and Spain.
“The newest campaign by Anatsa reveals the evolving menace landscape that banks and fiscal establishments experience in present day electronic world,” ThreatFabric stated. “The latest Google Participate in Retail store distribution campaigns […] exhibit the enormous possible for cellular fraud and the require for proactive measures to counter these kinds of threats.”
Discovered this posting exciting? Comply with us on Twitter and LinkedIn to read far more special content we article.
Some parts of this article are sourced from:
thehackernews.com


 New Fortinet’s FortiNAC Vulnerability Exposes Networks to Code Execution Attacks
New Fortinet’s FortiNAC Vulnerability Exposes Networks to Code Execution Attacks