Threat actors can choose advantage of Amazon Web Expert services Security Token Provider (AWS STS) as a way to infiltrate cloud accounts and perform abide by-on assaults.
The assistance permits danger actors to impersonate user identities and roles in cloud environments, Crimson Canary scientists Thomas Gardner and Cody Betsworth reported in a Tuesday investigation.
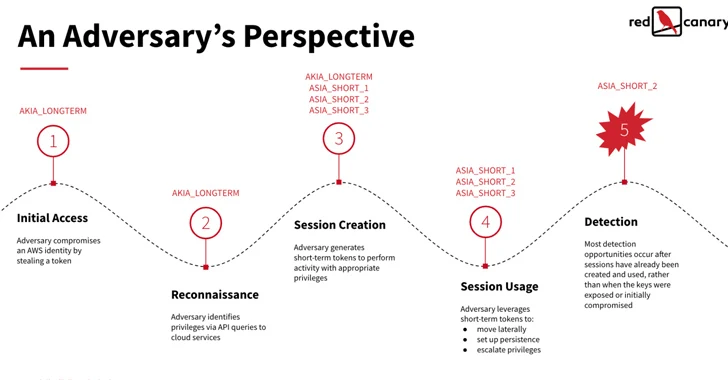
AWS STS is a web company that enables buyers to ask for short-term, restricted-privilege credentials for customers to accessibility AWS means with out needing to produce an AWS identity. These STS tokens can be valid any where from 15 minutes to 36 hours.
Danger actors can steal extensive-phrase IAM tokens through a range of solutions like malware bacterial infections, publicly exposed credentials, and phishing emails, subsequently working with them to identify roles and privileges connected with people tokens through API calls.

“Relying on the token’s authorization degree, adversaries may also be capable to use it to generate further IAM users with extensive-term AKIA tokens to assure persistence in the event that their preliminary AKIA token and all of the ASIA short term tokens it produced are found and revoked,” the researcher stated.
In the following stage, an MFA-authenticated STS token is employed to develop various new short-expression tokens, adopted by conducting post-exploitation actions these as facts exfiltration.
To mitigate this sort of AWS token abuse, it truly is recommended to log CloudTrail party information, detect position-chaining gatherings and MFA abuse, and rotate extended-expression IAM consumer obtain keys.
“AWS STS is a critical security handle for restricting the use of static credentials and the duration of entry for users across their cloud infrastructure,” the researchers reported.
“However, underneath selected IAM configurations that are popular across quite a few organizations, adversaries can also make and abuse these STS tokens to access cloud resources and carry out destructive actions.”
Located this article exciting? Observe us on Twitter and LinkedIn to go through much more exceptional material we post.
Some parts of this article are sourced from:
thehackernews.com

 New Report: Unveiling the Threat of Malicious Browser Extensions
New Report: Unveiling the Threat of Malicious Browser Extensions