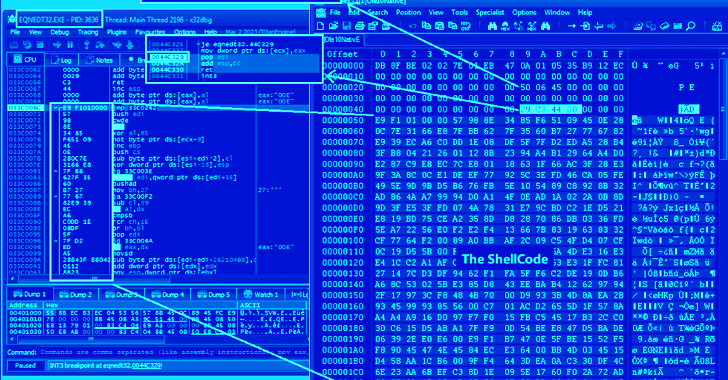
The Iranian threat actor tracked as APT34 has been connected to a new phishing attack that potential customers to the deployment of a variant of a backdoor known as SideTwist.
“APT34 has a higher level of attack technology, can design and style diverse intrusion methods for distinctive sorts of targets, and has provide chain attack ability,” NSFOCUS Security Labs mentioned in a report posted past 7 days.
APT34, also acknowledged by the names Cobalt Gypsy, Hazel Sandstorm (previously Europium), Helix Kitten, and OilRig, has a track history of focusing on telecommunications, government, defense, oil and economic products and services verticals in the Middle East given that at minimum 2014 by means of spear-phishing lures that culminate in the deployment of a variety of backdoors.

One particular of the key characteristics of the hacking outfit is its means to generate new and up-to-date tools to lower the odds of detection and obtain a foothold on compromised hosts for extended durations of time.
SideTwist was very first documented as utilized by APT34 in April 2021, with Check Place describing it as an implant able of file down load/add and command execution.
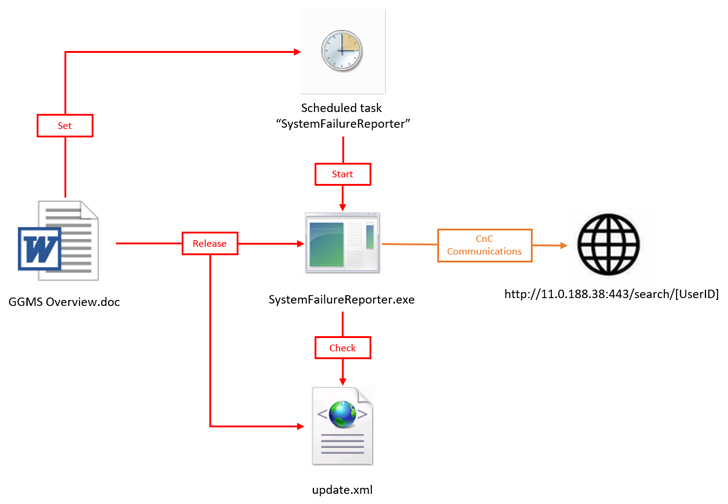
The attack chain determined by NSFOCUS commences with a bait Microsoft Word doc that embeds inside a destructive macro, which, in flip, extracts and launches the Base64-encoded payload stored in the file.
The payload is a variant of SideTwist which is compiled working with GCC and establishes conversation with a remote server (11..188[.]38) to obtain further commands.
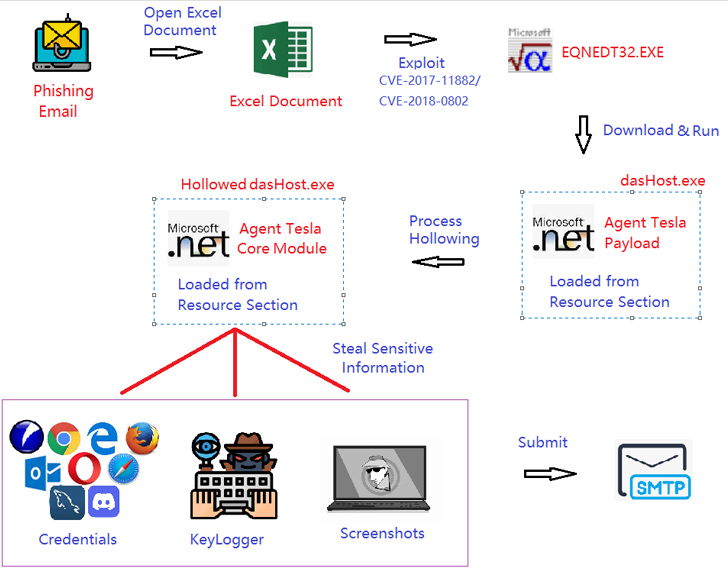
The development comes as Fortinet FortiGuard Labs captured a phishing campaign that spreads a new Agent Tesla variant employing a specifically crafted Microsoft Excel doc that exploits CVE-2017-11882, a six-year-old memory corruption vulnerability in Microsoft Office’s Equation Editor, and CVE-2018-0802.
Future WEBINARWay Much too Susceptible: Uncovering the Condition of the Identity Attack Area
Attained MFA? PAM? Assistance account safety? Obtain out how properly-outfitted your group really is in opposition to identification threats
Supercharge Your Competencies
“The Agent Tesla main module collects sensitive facts from the victim’s product,” security researcher Xiaopeng Zhang mentioned. “This info involves the saved credentials of some software, the victim’s keylogging facts, and screenshots.”
In accordance to facts shared by cybersecurity company Qualys, CVE-2017-11882 remains a person of the most favored flaws to day, exploited by “467 malware, 53 risk actors, and 14 ransomware” as lately as August 31, 2023.
It also follows the discovery of one more phishing attack that has been observed to utilize ISO graphic file lures to start malware strains these as Agent Tesla, LimeRAT, and Remcos RAT on infected hosts.
Located this posting attention-grabbing? Observe us on Twitter and LinkedIn to read extra special material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Three CISOs Share How to Run an Effective SOC
Three CISOs Share How to Run an Effective SOC