Cybersecurity researchers have detected in the wild yet one more variant of the Phobos ransomware loved ones known as Faust.
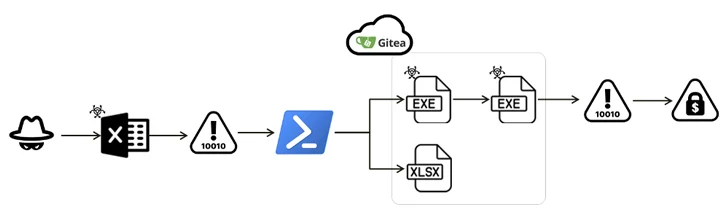
Fortinet FortiGuard Labs, which comprehensive the most recent iteration of the ransomware, reported it can be becoming propagated by indicates of an infection that provides a Microsoft Excel doc (.XLAM) containing a VBA script.
“The attackers used the Gitea assistance to retailer several files encoded in Foundation64, each and every carrying a malicious binary,” security researcher Cara Lin stated in a complex report revealed past week. “When these files are injected into a system’s memory, they initiate a file encryption attack.”
Faust is the most recent addition to numerous ransomware variants from the Phobos relatives, like Eking, 8, Elbie, Devos, and 8Foundation. It’s well worth noting that Faust was beforehand documented by Cisco Talos in November 2023.
The cybersecurity business described the variant as lively considering the fact that 2022 and “does not focus on distinct industries or regions.”

The attack chain commences with an XLAM document that, when opened, downloads Base64-encoded information from Gitea in get to preserve a harmless XLSX file, when also stealthily retrieving an executable that masquerades as an updater for the AVG AntiVirus software program (“AVG updater.exe”).
The binary, for its aspect, capabilities as a downloader to fetch and start a further executable named “SmartScreen Defender Windows.exe” in purchase to kick-commence its encryption course of action by using a fileless attack to deploy the destructive shellcode.
“The Faust variant exhibits the means to keep persistence in an setting and makes multiple threads for successful execution,” Lin said.
The development comes as new ransomware families this kind of as Albabat (aka White Bat), Kasseika, Kuiper, Mimus, and NONAME have acquired traction, with the former a Rust-centered malware that is distributed in the type of fraudulent software program such as a phony Windows 10 digital activation software and a cheat method for the Counter-Strike 2 sport.
Trellix, which examined the Windows, Linux, and macOS variations of Kuiper previously this thirty day period, attributed the Goland-dependent ransomware to a menace actor named RobinHood, who first marketed it on underground discussion boards in September 2023.
“The concurrency focused character of Golang benefits the threat actor here, averting race circumstances and other typical complications when dealing with multiple threads, which would have usually been a (in close proximity to) certainty,” security researcher Max Kersten stated.
“One more aspect that the Kuiper ransomware leverages, which is also a reason for Golang’s elevated popularity, are the language’s cross-system capabilities to develop builds for a wide variety of platforms. This overall flexibility permits attackers to adapt their code with little energy, specially given that the the vast majority of the code base (i.e., encryption-related exercise) is pure Golang and requires no rewriting for a different platform.”
NONAME is also noteworthy for the reality that its data leak web page imitates that of the LockBit group, boosting the likelihood that it could both be yet another LockBit or that it collects leaked databases shared by LockBit on the formal leak portal, researcher Rakesh Krishnan pointed out.
The findings comply with a report from French cybersecurity enterprise Intrinsec that linked the nascent 3AM (also spelled ThreeAM) ransomware to the Royal/BlackSuit ransomware, which, in change, emerged following the shutdown of the Conti cybercrime syndicate in May perhaps 2022.

The links stem from a “considerable overlap” in methods and communication channels involving 3 AM ransomware and the “shared infrastructure of ex-Conti-Ryuk-TrickBot nexus.”
That’s not all. Ransomware actors have been observed once once again applying TeamViewer as an initial entry vector to breach target environments and endeavor to deploy encryptors based on the LockBit ransomware builder, which leaked in September 2022.

“Threat actors glance for any readily available signifies of obtain to particular person endpoints to wreak havoc and potentially prolong their reach further more into the infrastructure,” cybersecurity company Huntress stated.
In latest months, LockBit 3. has also been distributed in the form of Microsoft Word data files disguised as resumes focusing on entities in South Korea, in accordance to the AhnLab Security Intelligence Centre (ASEC).
Observed this post attention-grabbing? Follow us on Twitter and LinkedIn to read additional exceptional written content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 NSA Admits Secretly Buying Your Internet Browsing Data without Warrants
NSA Admits Secretly Buying Your Internet Browsing Data without Warrants