The danger actors at the rear of the KV-botnet designed “behavioral variations” to the destructive network as U.S. law enforcement commenced issuing commands to neutralize the activity.
KV-botnet is the identify offered to a network of compromised modest business office and household business (SOHO) routers and firewall devices across the world, with one specific cluster acting as a covert information transfer process for other Chinese condition-sponsored actors, together with Volt Storm (aka Bronze Silhouette, Insidious Taurus, or Vanguard Panda).
Active because at least February 2022, it was initial documented by the Black Lotus Labs workforce at Lumen Systems in mid-December 2023. The botnet is recognized to comprise two major sub-teams, viz. KV and JDY, with the latter principally utilized for scanning potential targets for reconnaissance.
Late last month, the U.S. authorities declared a court docket-licensed disruption hard work to choose down the KV cluster, which is ordinarily reserved for handbook operations from substantial-profile targets chosen immediately after broader scanning through the JDY sub-group.

Now, in accordance to new conclusions from the cybersecurity firm, the JDY cluster fell silent for roughly fifteen days following general public disclosure and as a byproduct of the U.S. Federal Bureau of Investigation (FBI) enterprise.
“In mid-December 2023, we noticed this action cluster hovering about 1500 energetic bots,” security researcher Ryan English stated. “When we sampled the size of this cluster in mid-January 2024 its dimension dwindled to around 650 bots.”
Offered that the takedown actions began with a signed warrant issued on December 6, 2023, it is good to suppose that the FBI started transmitting instructions to routers situated in the U.S. someday on or following that date to wipe the botnet payload and stop them from currently being re-contaminated.
“We noticed the KV-botnet operators start to restructure, committing 8 straight several hours of exercise on December 8, 2023, approximately ten hrs of functions the next working day on December 9, 2023, adopted by a person hour on December 11, 2023,” Lumen claimed in a technical report shared with The Hacker Information.
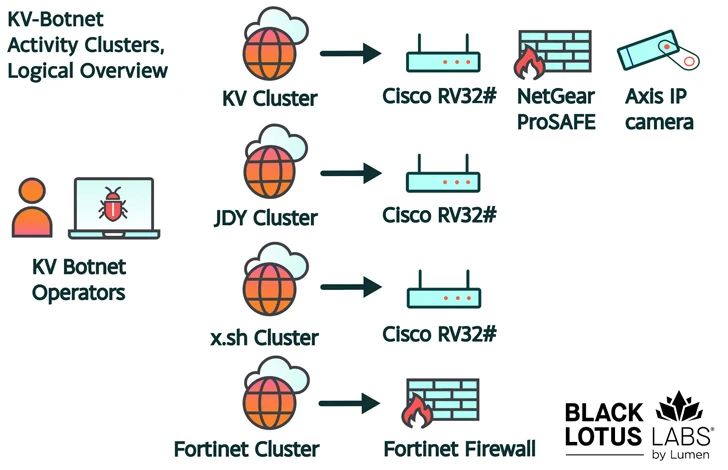
Throughout this 4-day period of time, the threat actor was spotted interacting with 3,045 unique IP addresses that ended up associated with NETGEAR ProSAFEs (2,158), Cisco RV 320/325 (310), Axis IP cameras (29), DrayTek Vigor routers (17), and other unidentified gadgets (531).
Also observed in early December 2023 was a substantial spike in exploitation attempts from the payload server, indicating the adversary’s most likely makes an attempt to re-exploit the gadgets as they detected their infrastructure heading offline. Lumen said it also took methods to null-route a further established of backup servers that grew to become operational about the exact time.

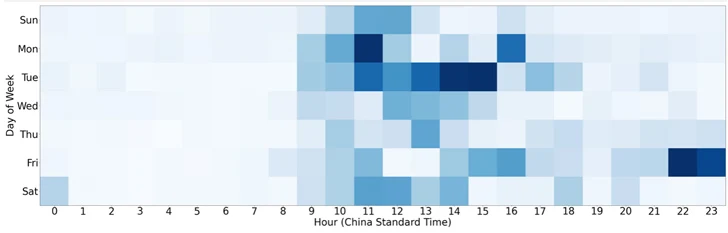
It is really value noting that the operators of the KV-botnet are known to conduct their individual reconnaissance and targeting while also supporting a number of groups like Volt Typhoon. Apparently, the timestamps linked with exploitation of the bots correlates to China functioning hours.
“Our telemetry indicates that there have been administrative connections into the regarded payload servers from IP addresses affiliated with China Telecom,” Danny Adamitis, principal facts security engineer at Black Lotus Labs, instructed The Hacker Information.
What’s far more, the statement from the U.S. Justice Department explained the botnet as managed by “People’s Republic of China (PRC) condition-sponsored hackers.”
This raises the likelihood that the botnet “was created by an business supporting the Volt Storm hackers while if the botnet was designed by Volt Hurricane, we suspect they would have explained ‘nation-state’ actors,” Adamitis additional.
There are also indications that the menace actors established a 3rd related-but-unique botnet cluster dubbed x.sh as early as January 2023 that is composed of infected Cisco routers by deploying a web shell named “fys.sh,” as highlighted by SecurityScorecard very last month.

But with KV-botnet currently being just “just one kind of infrastructure used by Volt Hurricane to obfuscate their action,” it is expected that the new wave of steps will prompt the point out-sponsored actors to presumably changeover to a different covert network in get to meet their strategic ambitions.
“A significant percent of all networking equipment in use close to the environment is performing completely nicely, but is no longer supported,” English mentioned. “Close customers have a hard economical choice when a system reaches that stage, and lots of are not even conscious that a router or firewall is at the stop of its supported lifetime.
“Innovative risk actors are well conscious that this signifies fertile floor for exploitation. Replacing unsupported equipment is generally the ideal option, but not generally feasible.”
“Mitigation involves defenders incorporating their edge products to the prolonged checklist of all those they now have to patch and update as frequently as readily available, rebooting devices and configuring EDR or SASE options where by applicable, and keeping an eye on significant information transfers out of the network. Geofencing is not a defense to depend on, when the risk actor can hop from a close by place.”
Uncovered this write-up fascinating? Abide by us on Twitter and LinkedIn to read through far more distinctive content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Critical Bootloader Vulnerability in Shim Impacts Nearly All Linux Distros
Critical Bootloader Vulnerability in Shim Impacts Nearly All Linux Distros