The menace actors at the rear of the 8Foundation ransomware are leveraging a variant of the Phobos ransomware to conduct their economically determined assaults.
The results come from Cisco Talos, which has recorded an enhance in activity carried out by cybercriminals.
“Most of the group’s Phobos variants are dispersed by SmokeLoader, a backdoor trojan,” security researcher Guilherme Venere said in an exhaustive two-portion evaluation released Friday.
“This commodity loader commonly drops or downloads extra payloads when deployed. In 8Base strategies, nevertheless, it has the ransomware element embedded in its encrypted payloads, which is then decrypted and loaded into the SmokeLoader process’ memory.”
8Foundation arrived into sharp target in mid-2023, when a related spike in exercise was noticed by the cybersecurity neighborhood. It can be claimed to be active at minimum due to the fact March 2022.
A previous evaluation from VMware Carbon Black in June 2023 determined parallels amongst 8Base and RansomHouse, in addition to exploring a Phobos ransomware sample that was discovered making use of the “.8foundation” file extension for encrypted files.
This elevated the probability that 8Base is both a successor to Phobos or that the danger actors driving the procedure are basically applying presently existing ransomware strains to carry out their assaults, akin to the Vice Society ransomware group.

The hottest results from Cisco Talos demonstrate that SmokeLoader is applied as a launchpad to execute the Phobos payload, which then carries out ways to establish persistence, terminate processes that may perhaps preserve the focus on data files open up, disable technique recovery, and delete backups as very well as shadow copies.
One more notable attribute is the comprehensive encryption of documents that are down below 1.5 MB and partial encryption of information earlier mentioned the threshold to velocity up the encryption course of action.
Furthermore, the artifact incorporates a configuration with around 70 options that’s encrypted employing a tough-coded key. The configuration unlocks supplemental characteristics this kind of as Consumer Account Command (UAC) bypass and reporting of a victim infection to an external URL.
There is also a really hard-coded RSA essential utilized to secure the for each-file AES key made use of in the encryption, which Talos claimed could enable enable decryption of files locked by the ransomware.
“The moment each and every file is encrypted, the critical utilized in the encryption alongside with added metadata is then encrypted utilizing RSA-1024 with a difficult-coded community vital, and saved to the conclude of the file,” Venere elaborated.
“It implies, however, that once the personal RSA crucial is known, any file encrypted by any Phobos variant since 2019 can reliably be decrypted.”
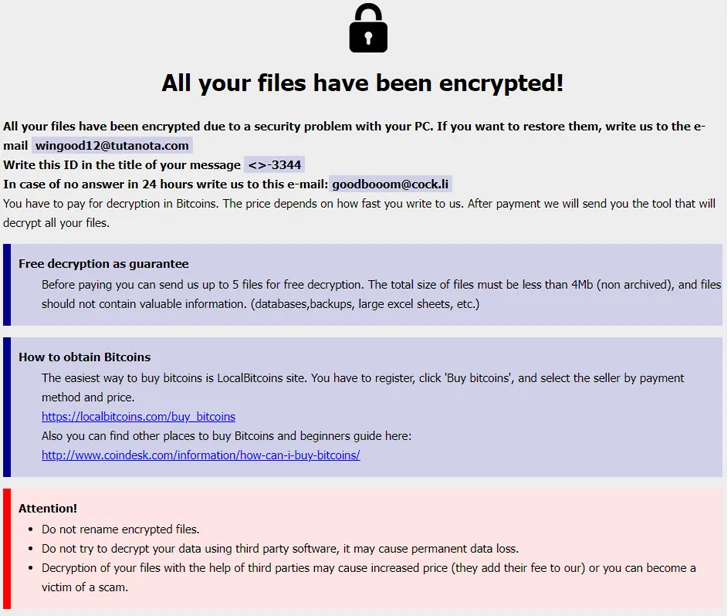
Phobos, which initially emerged in 2019, is an evolution of the Dharma (aka Crysis) ransomware, with the ransomware predominantly manifesting as the variants Eking, Eight, Elbie, Devos, and Faust, dependent on the quantity of artifacts unearthed on VirusTotal.
“The samples all contained the exact supply code and ended up configured to avoid encrypting data files that other Phobos affiliated previously locked, but the configuration modified a bit depending on the variant being deployed,” Venere stated. “This is based on a file extension block listing in the ransomware’s configuration settings.”
Cisco Talos assesses that Phobos is intently managed by a central authority, when currently being bought as a ransomware-as-a-assistance (RaaS) to other affiliate marketers based mostly on the similar RSA general public essential, the versions in the call email messages, and normal updates to the ransomware’s extension block lists.
“The extension blocklists surface to convey to a tale of which teams utilised that exact foundation sample above time,” Venere mentioned.
“The extension block lists discovered in the a lot of Phobos samples […] are continually up to date with new information that have been locked in earlier Phobos campaigns. This may well help the strategy that there is a central authority behind the builder who keeps keep track of of who utilised Phobos in the earlier. The intent could be to stop Phobos affiliates from interfering with a single another’s functions.”
The advancement comes as FalconFeeds disclosed that a danger actor is marketing a advanced ransomware product termed UBUD that is developed in C and functions “powerful anti-detection steps from virtual machines and debugging instruments.”

It also follows a formal grievance filed by the BlackCat ransomware team with the U.S. Securities and Trade Commission (SEC), alleging that a single of its victims, MeridianLink, failed to comply with new disclosure regulations that demand impacted corporations to report the incident within just four business enterprise times, DataBreaches.net noted.
The financial software package corporation has considering the fact that verified it was qualified in a cyber attack on November 10, but pointed out it observed no proof of unauthorized accessibility to its devices.
When the SEC disclosure rules you should not consider result right until next month on December 18, the unconventional stress tactic is a indicator that danger actors are carefully seeing the room and are keen to bend governing administration rules to their advantage and compel victims to pay out up.
That claimed, it can be worthy of noting that the enforcement solely applies in circumstances exactly where the corporations have discovered that the attacks have had a “material” affect on their bottom strains.
Another prolific ransomware gang LockBit, in the in the meantime, has instituted new negotiation guidelines starting off October 2023, citing significantly less-than-expected settlements and larger sized savings made available to victims because of to the “different stages of practical experience of affiliate marketers.”
“Build a bare minimum ransom request relying on the company’s yearly profits, for case in point at 3%, and prohibit discount rates of far more than 50%,” the LockBit operators said, according to a in-depth report from Analyst1.
“Hence, if the firm’s income is $100 million USD, the first ransom ask for should really start from $3 million USD with the closing payout have to be no a lot less than $1.5 million USD.”
Discovered this article fascinating? Comply with us on Twitter and LinkedIn to examine a lot more unique articles we publish.
Some parts of this article are sourced from:
thehackernews.com


 Russian Cyber Espionage Group Deploys LitterDrifter USB Worm in Targeted Attacks
Russian Cyber Espionage Group Deploys LitterDrifter USB Worm in Targeted Attacks