We analyzed 2,5 million vulnerabilities we uncovered in our customer’s property. This is what we located.
Digging into the data
The dataset we review listed here is representative of a subset of purchasers that subscribe to our vulnerability scanning solutions. Belongings scanned involve individuals reachable throughout the Internet, as nicely as individuals present on inner networks. The details includes findings for network gear, desktops, web servers, database servers, and even the odd doc printer or scanning gadget.
The selection of businesses in this dataset is more compact (3 considerably less) than the preceding dataset used in final year’s Security Navigator 2023 and some companies were being replaced by new additions. With the alter of businesses will come a various combine of assets, which leaves comparing the preceding results akin to comparing apples to oranges (we may be biased), but it is continue to worth noting very similar designs exactly where probable.
This calendar year, we revisit the menacing vulnerability topic with an eye on the ever-present and lingering tail of unresolved program weaknesses. The waves of recently uncovered serious issues are just for our focus with current unresolved issues, seeming like a hydra that retains on expanding new snaking heads as soon as you dispatch some others.
Examining whether or not a method is adequately shielded is a challenge that necessitates talent and skills and can just take a whole lot of time. But we want to discover of any weaknesses beforehand fairly than possessing to deal with the fallout of an unplanned “free of charge pentest” by a random Cy-X group.
Security Navigator 2024 is In this article – Obtain Now#
The recently released Security Navigator 2024 presents critical insights into recent digital threats, documenting 129,395 incidents and 25,076 verified breaches. Extra than just a report, it serves as a guidebook to navigating a safer digital landscape.
What is Inside of?#
- 📈 In-Depth Analysis: Discover developments, attack designs, and predictions. Find out from scenario experiments in CyberSOC and Pentesting.
- 🔮 Long run-All set: Equip on your own with our security predictions and investigation summary.
- 👁️ True-Time Info: From Dark Net surveillance to industry-distinct studies.
Continue to be a person step ahead in cybersecurity. Your important tutorial awaits!
🔗 Get Your Copy Now
Vulnerability Scanning Findings by Severity
Analyzing the severity ranking share for every distinctive Locating we see that the bulk of exceptional Conclusions, 79%, are categorized as ‘High’ or ‘Medium’. However, it is also well worth noting that 50 percent, 50.4%, of unique Findings are regarded as ‘Critical’ or ‘High.’
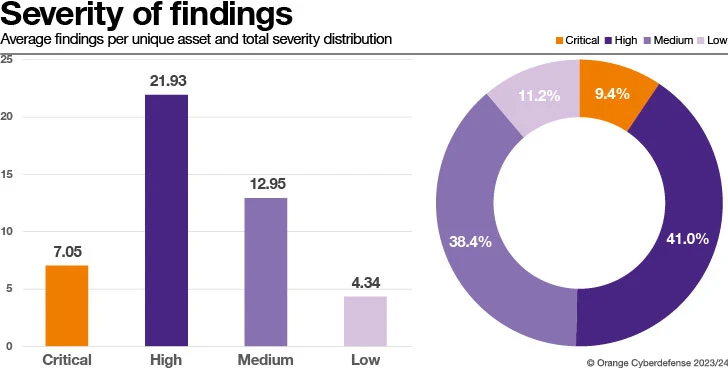
The regular amount of ‘Critical’ or ‘High’ Conclusions has lessened by 52.17% and 43.83%, respectively, when compared to our beforehand printed benefits. An enhancement can also be noticed for Conclusions with severity ratings ‘Medium’ and ‘Low’ currently being down 29.92% and 28.76%. As this report makes use of a a bit unique sample of clients to past year, a YoY comparison has confined price, but we see proof that shoppers are responding perfectly to the findings we report, ensuing in an over-all enhancement.
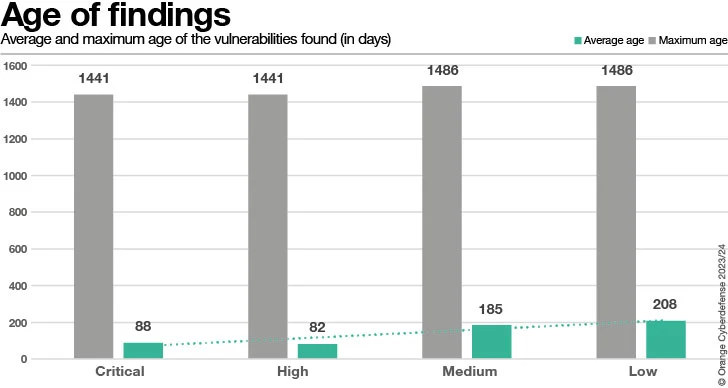
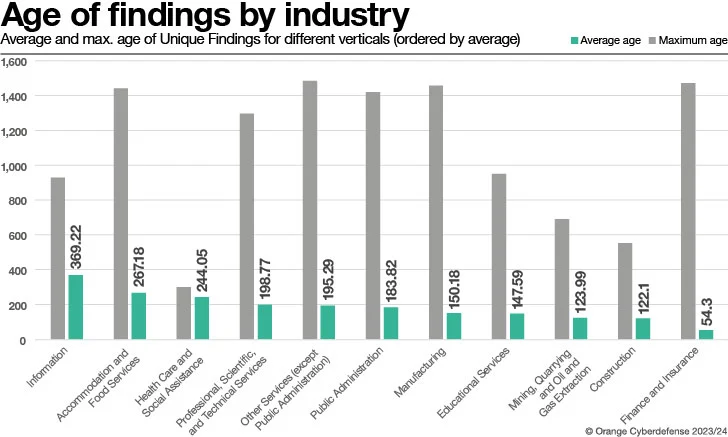
The the greater part of Results (78%) rated ‘Critical’ or ‘High’ are 30 days or more youthful (when looking at a 120-day window). Conversely, 18% of all conclusions rated ‘Critical’ or ‘High’ are 150-times or older. From a prioritization perspective, ‘Critical’ or ‘High’ true findings appear to be dealt with quickly, but some residual continue to accumulates more than time. We see, therefore, that unresolved Conclusions continue to increase more mature. Certainly, ~35% of all exceptional CVEs are from results 120 days or more mature.
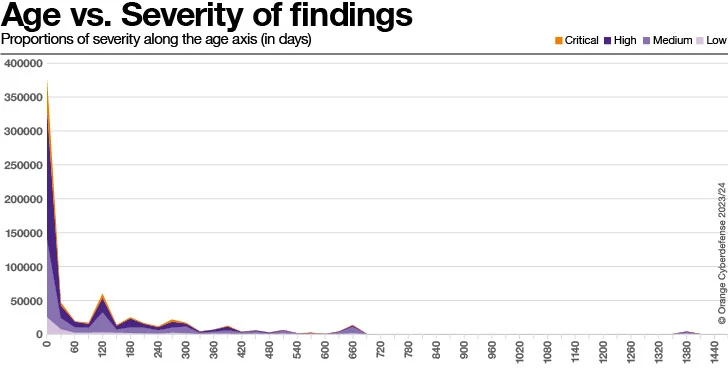
The chart earlier mentioned exhibits the prolonged tail of unresolved true conclusions. Take note the to start with extraordinary lengthy tail peak about 660 days and the next just one at 1380 days (3 many years and 10 months).
A window of prospect

The higher typical figures of ‘Critical’ and ‘High’ findings are mostly affected by belongings functioning Microsoft Windows or Microsoft Windows Server running devices. Property running functioning techniques other than Microsoft, this sort of as Linux-centered OS, are existing, but these are reported proportionally much a lot less.
We really should be aware, on the other hand, that the ‘Critical’ or ‘High’ findings related with belongings operating Windows are not necessarily vulnerabilities in the functioning process but can also be associated to applications running on the asset.
It is perhaps comprehensible that unsupported Microsoft Windows and Windows Server variations are outstanding right here, but it is surprising to discover much more modern variations of these functioning techniques with severities rated as ‘Critical’ or ‘High’.
Industry point of view
We are applying NAICS for our sector classification. The results below only look at Results primarily based on scans of hosts rather than expert services this sort of as web apps. The average exclusive actual Getting per one of a kind asset is 31.74 across all organizations, denoted by the dashed horizontal line in the chart under.
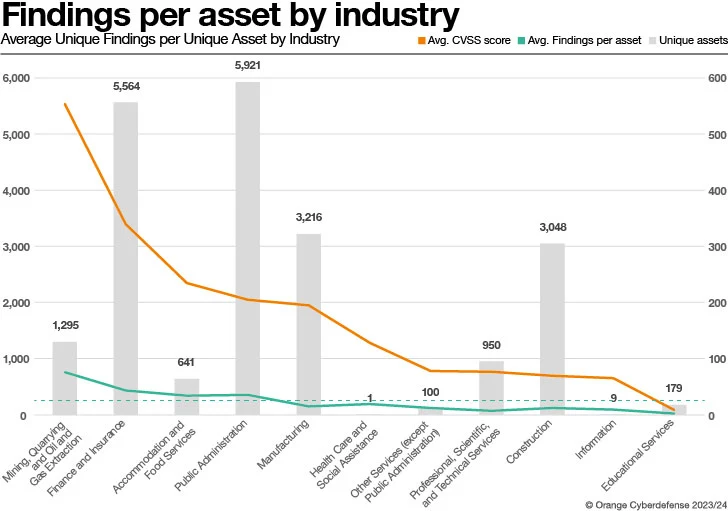
Our consumers in the Development field look to be doing exceptionally well compared to clients in other industries, with an typical of 12.12 Conclusions for each Asset. At the opposite conclusion of the spectrum, we have the Mining, Quarrying, and Oil and Gas industries, where we report an regular of 76.25 special conclusions for each asset. Purchasers in Community Administration amazed us by outperforming Finance and Insurance policy with an ordinary of 35.3 Findings per Asset, as opposed with 43.27, irrespective of the more substantial amount of Property. Of course, these values are derived from the set of consumers current in our sample and may perhaps not represent the common reality.
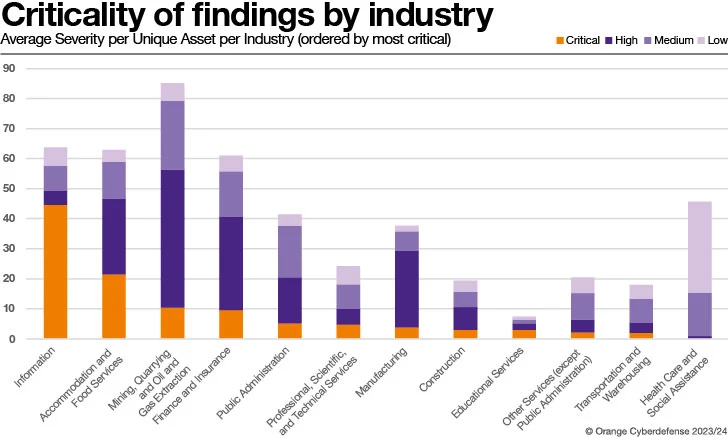
When comparing the average severity for every unique asset per Field, we see a combined picture. We can overlook Well being Care and Social Guidance and Information, with a rather tiny exceptional asset rely, that effects in averages that are disproportionate in relation to other Industries.
Our over-all Field normal for Severity rating Significant is 21.93 and Mining, Quarrying and Oil and Fuel Extraction have much more than double that typical.
In the same way, Finance and Insurance plan with Lodging and Foods Solutions also overshot the in general common by 10.2 and 3.4 conclusions for each special asset, respectively. The exact 3 Industries exceeded the in general typical for findings rated Critical, with Lodging and Foodstuff Servers accomplishing so by almost a issue of 3.
Vulnerability is finding aged
As we revisit the menacing vulnerability concept this calendar year, we when once more glimpse suspiciously at the ever-existing and lingering tale of unresolved program weaknesses that are just receiving more mature. We assessed above 2.5m vulnerability conclusions that we reported to our clientele and about 1,500 reports from our experienced moral hackers to realize the existing point out of security vulnerabilities and contemplate their role and success as a tool for prioritization.
The bulk of exceptional Results documented by our scanning teams – 79% – are categorised as ‘High’ or ‘Medium,’ and 18% of all severe findings are 150 times or more mature. Though these are commonly dealt with much more quickly than other people, some residuals still accumulate over time. Although most results we detect are settled after 90 times, 35% of all findings we report persist for 120 times or for a longer time. And way much too many are under no circumstances dealt with at all.
Our scanning final results illuminate the persistent dilemma of unpatched vulnerabilities. In the meantime, our Ethical Hacking teams more regularly experience newer programs and methods developed on modern day platforms, frameworks, and languages.
The position of the Ethical Hacker is to conduct Penetration Tests – to emulate a destructive attacker and evaluate a system, application, system, or even folks for vulnerabilities that could be utilized to achieve entry or deny access to IT methods.
Penetration Tests is typically thought of a element of Vulnerability Management but could also be seen as a kind of Menace Intelligence that organizations should leverage as part of their proactive defense approach.
17.67% of results our Moral Hackers reported ended up rated as ‘Serious’, but, on a brighter observe, hackers will have to operate more difficult these days to find out them than they had to in the past.
This is just an excerpt of the examination. Much more specifics on our evaluation of vulnerabilities and Pentesting (as properly as a ton of other fascinating study matters like VERIS categorization of the incidents taken care of in our CyberSOCs, Cyber Extortion studies and an investigation of Hacktivism) can be located in the Security Navigator. Just fill in the variety and get your obtain. It is truly worth it!
Be aware: This instructive piece has been expertly crafted and generously shared by Charl van der Walt, Head of the Security Study Centre, Orange Cyberdefense.
Discovered this article attention-grabbing? Observe us on Twitter and LinkedIn to examine much more special content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 FTC Bans InMarket for Selling Precise User Location Without Consent
FTC Bans InMarket for Selling Precise User Location Without Consent