For as well long the cybersecurity planet centered completely on data technology (IT), leaving operational technology (OT) to fend for by itself. Ordinarily, couple industrial enterprises experienced committed cybersecurity leaders. Any security choices that arose fell to the plant and manufacturing unit professionals, who are very experienced specialized gurus in other spots but often deficiency cybersecurity schooling or knowledge.
In more latest decades, an uptick in cyberattacks in opposition to industrial amenities and the development of IT/OT convergence pushed by Field 4. have highlighted the vacuum of possession all over OT security. According to a new Fortinet report, most businesses are wanting to Chief Info Security Officers (CISOs) to fix the difficulty.
The good news is, CISOs are no strangers to improve or complicated challenges. The situation itself is less than 20 a long time previous, however in individuals two many years CISOs have navigated some of the most disruptive cybersecurity events that were certainly watershed times in technology.
Even now, most CISOs have built their mark securing IT environments — and IT security strategies and applications hardly ever translate to an OT context. Although the tender expertise of collaboration and group-developing will undoubtedly support CISOs as they provide the manufacturing facility flooring into their realm of accountability, they need to also make a concentrated hard work to have an understanding of the OT landscape’s unique topography and unique security troubles.
Basic safety around almost everything
The CIA triad — Confidentiality, Integrity & Availability — is a key notion in cybersecurity. Critically, IT and OT prioritize the things of the triad in different ways — whilst security is often the typical denominator.
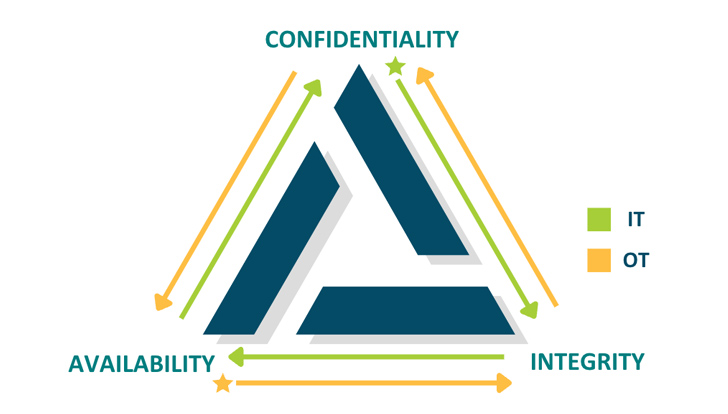 Image 1: The CIA triad of IT security is reversed in the OT planet, in which availability is the maximum priority.
Image 1: The CIA triad of IT security is reversed in the OT planet, in which availability is the maximum priority.
- In IT, security usually means that facts is guarded by means of confidentiality. People get harm when their delicate, personal facts is compromised. For the enterprise, securing information saves them from breaches, fines, and reputational harm.
- In OT, protection implies that cyber-actual physical techniques are dependable and responsive. Individuals get harm when a blast furnace or an industrial boiler does not functionality effectively. For the enterprise, availability retains devices operating on time down to the millisecond, which makes sure productivity and profitability.
Somewhat ironically, the AIC triad of the OT globe has resulted in devices and resources that prioritize bodily basic safety but normally appear with handful of or no cybersecurity attributes at all. It will be the CISO’s responsibility to detect and implement security methods that safeguard OT devices from cyberthreats without having disrupting their operations.
.xm_container show: flex align-merchandise: heart margin: 20px 10px 30px qualifications: #f9fbff colour: #160755 padding: 5% border: 2px stable #d9deff border-radius: 10px textual content-align: left box-shadow:6px 6px #e2ebff -webkit-border-major-still left-radius: 25px -moz-border-radius-topleft: 25px -webkit-border-base-proper-radius: 25px -moz-border-radius-bottomright: 25px .e book-picture flex: 200px margin-right: 20px padding: 20px .e book-aspects flex: 1 .ebook-particulars ul margin: 15px .e-book-details ul li margin-bottom: 5px @media (max-width: 600px) .xm_container flex-path: column .ebook-image margin-correct: margin-bottom: 20pxpadding: 20px

Pondering how to secure your industrial functions from prospective threats? This complete report on I-SRA has the answers. Uncover the best issues, which includes operational basic safety pitfalls and Advanced Persistent Threats (APTs). Down load the report right now!
Levels of segmentation
In both equally OT and IT, segmentation boundaries the network’s attack area. In OT, the Purdue Design serves as a framework for how and why devices can and really should connect with just about every other.
In a highly simplified nutshell, the Purdue Model comprises five layers.
- Ranges 4 and 5 are the outermost layers that include things like web and email servers, IT infrastructure, and customers firewalling in remotely.
- Amounts 2 and 3 are the operational levels that function the computer software and apps that operate OT environments.
- Stages and 1 keep the products, sensors, programmable logic controllers (PLCs), and distributed regulate devices (DCS) that do the actual function and have to be secured from outside the house interference.
The function of these levels is to generate the two reasonable and physical separation in between approach stages. The closer you get to the cyber-bodily operation of industrial techniques like injectors, robotic arms, and industrial presses, the additional checks and balances are in area to shield them.
Even though the notion of segmentation will not be new to CISOs, they will have to have to realize that the separation of zones is a great deal stricter in OT environments and should be enforced at all occasions. Industrial enterprises adhere to the Purdue design or other equivalent frameworks to be certain protection and security and to meet up with lots of regulatory compliance mandates.
Downtime is not an option
In IT, downtime for updates and patches is no huge offer, specially in a Program-as-a-Service (SaaS) planet exactly where new updates are released practically in real time.
Regardless of whether for security or income, OT systems are often up and running. They simply cannot be stopped or paused to down load a new running method or implement even a critical patch. Any process that requires downtime is basically a non-starter for the large the vast majority of OT systems. For this motive, CISOs really should not be surprised to explore a long time-aged devices (probable working on software package that attained its close-of-lifestyle day very long ago) that even now serve as a vital piece of the operation.
The problem dealing with CISOs will be to recognize security controls that will not interrupt or interfere with fragile OT processes. The ideal solutions will “wrap” the existing OT infrastructure in a layer of security that protects critical processes without the need of altering, complicating, or crowding them.
All entry is “remote” obtain
Typically, OT programs have been secured as a result of isolation. Now that businesses are connecting these environments to capitalize on Market 4. or to let less difficult accessibility for contractors, all accessibility ought to be monitored, managed, and recorded.
- The IT environment is a electronic put the place business enterprise comes about. Enterprise people carry out their operate and techniques exchange details all in just this place, working day in and day out. To place it a different way, human beings are intended to actively participate in and make alterations to the IT environment.
- OT devices and environments are developed to run without having human intervention — “established it and forget it.” Human beings are meant to established them up and then let them run. End users do not stay logged into an OT ecosystem all working day the way organization people would in an IT method.
In this context, anyone accessing the OT natural environment is effectively an outsider. No matter whether it is a vendor connecting remotely, a business enterprise user coming in by means of the IT network, or even an OT operator accessing the environment on-web-site, each individual link will come from the exterior. Recognizing this essential stage will aid CISOs to fully grasp that industrial secure remote entry (I-SRA) equipment should be applied for all entry eventualities, not only people that IT would think about to be “remote.”
IT instruments do not (often) function for OT
Tools designed for IT rarely at any time translate to OT.
- Essential capabilities like vulnerability scanning can interrupt OT processes and knock programs totally offline, and most equipment do not have more than enough CPU/RAM to assist endpoint security, anti-virus, or other brokers.
- Most IT instruments route targeted visitors by the cloud. In OT, this can compromise availability and can’t support the several unconnected elements common to OT environments.
- The existence cycles of IT equipment are ordinarily considerably shorter than the life cycles of OT units. Because of to the often-up character of OT environments, any tool that wants repeated patching, updates, or downtime is not relevant.
Forcing IT-intended instruments into OT environments only adds complexity devoid of addressing the essential security requirements and priorities of these environments. The quicker a CISO realizes that OT methods are entitled to security answers made for their distinctive wants, the speedier they will be on their way to utilizing the finest instruments and insurance policies.
Tender capabilities are the keys to CISO good results
Specified that most cybersecurity leaders at present are likely to arrive from IT security roles, it will make feeling that numerous CISOs will have a (potentially unconscious) bias toward IT philosophies, tools, and tactics. To effectively safe OT environments, CISOs will need to become learners once more and lean on other people to understand what they do not still know.
The excellent information is that CISOs generally have a propensity to request the right queries and look for assist from the proper specialists even though however pushing the envelope and demanding good outcomes. At the conclude of the working day, a CISO’s job is to lead persons and groups of industry experts to complete the greater objective of securing the business and enabling the enterprise. All those inclined to bridge the OT security divide by means of potent management and a willingness to learn ought to speedily come across them selves on the road to achievements.
To learn about a true-environment solution that can support CISOs better safe their OT environment, discover Cyolo.
Uncovered this post attention-grabbing? Abide by us on Twitter and LinkedIn to read much more special articles we article.
Some parts of this article are sourced from:
thehackernews.com


 8Base Ransomware Spikes in Activity, Threatens U.S. and Brazilian Businesses
8Base Ransomware Spikes in Activity, Threatens U.S. and Brazilian Businesses