5G is a game changer for mobile connectivity, which includes mobile connectivity to the cloud. The technology provides large speed and reduced latency when connecting smartphones and IoT gadgets to cloud infrastructure. 5G networks are a critical aspect of all infrastructure layers concerning the conclude user and the finish company these networks transmit delicate information that can be critical for governments and companies, not to mention people today. As a outcome, 5G networks are a prime focus on for attackers. For this rationale, cybersecurity has been a key thing to consider in producing the 5G conventional.
5G encompasses robust security features that assurance confidentiality, integrity, and availability of network services and user facts. In this post, Seva Vayner, Product or service Owner of Gcore’s Edge Cloud services, presents a deep dive into five of 5 G’s reducing-edge security measures. He also delves into the pivotal functionality abilities of 5G, accompanied by use scenarios that show how modern, cloud-native enterprises can leverage this transformative technology to their edge.
What Is 5G
5G is the new conventional of wireless networks that supersedes 4G (LTE). It is intended to link individuals and gadgets at quickly speeds with very low latency.
The throughput of 5G considerably exceeds the throughput of 4G. In idea, 5G gives up to 20 Gbps in the downlink. In comparison, 4G only presents up to 100 Mbps, 200 periods a lot less than 5G. According to the 2023 CELLSMART study, in exercise, outdoor checks present that 5G operators in the US and EU offer shut to 1 Gbps for the downlink channel.
As for 5G latency, it can be up to 10 ms (vs. 30 ms in 4G)—but only in a test environment. In reality, latency depends on lots of factors. For case in point, Ericsson’s assessments in the US showed that 5G latency is normally all-around 20 ms but no additional than 50 ms, which is just about unnoticeable to human beings. This is fantastic news for gaming, the place latency larger than 50 ms is critical.
5 Will have to-Know Security Attributes of 5G
Vital 5G security techniques and technologies include encryption, privateness defense, authentication and authorization, network slicing, and network gear security assurance. Let’s seem at them in much more depth.
1. Encryption
Encryption shields user info and network targeted traffic from eavesdropping, interception, and tampering. 5G makes use of robust encryption algorithms this kind of as AES, ZUC, SNOW 3G, and HMAC-SHA-256. The encryption attributes contain a separation of the security keys in between the main network segments. Also supplied is quick synchronization of the security contexts in the access network (foundation stations) and the core network.
2. Privacy Protection
In 5G networks, privateness protection is ensured via the use of encryption and numerous other procedures. These methods effectively guard in opposition to important threats like IMSI/TMSI-catchers, which attackers frequently use to determine and keep track of network subscribers. Cellular operators can implement the Elliptic Curve Integrated Encryption Scheme system to conceal and on a regular basis update a subscriber’s non permanent identifier (TMSI). In addition, operators can detect fake base stations, which are normally the resource of IMSI/TMSI-catchers.
3. Authentication and Authorization
Authentication and authorization in 5G is based on the Authentication and Essential Settlement system (5G AKA). It contains a sturdy authentication mechanism to verify the identification of users, equipment, and network components. In contrast to 4G, 5G isn’t going to require actual physical SIM cards for credentials, but also supports pre-shared keys, certificates, and tokens. Cellular operators can decide on the authentication qualifications and authentication solutions greatest suited to their consumers and IoT devices. For case in point, standard SIM cards are suitable for mobile phones, though digital credentials are much more acceptable for simple IoT equipment geared up with eSIM.
4. Network Slicing
Network slicing will allow the generation of virtual networks for distinct providers and applications. For occasion, a subscribing firm can use 1 network slice for higher-priority workforce with obtain to corporate services, and one more slice for lower-priority IoT warehouse sensors that transmit data to storage in a community cloud. Each individual network slice can be assigned certain security policies and protocols, assisting to isolate and defend data and companies.
5. NESAS
NESAS, or the Network Tools Security Assurance Plan, makes certain the protected implementation of telecom devices that cellular operators use in their networks, such as 5G. Developed by 3GPP and GSMA, NESAS establishes security requirements and procedures for successful infrastructure audits. NESAS can take into account both equally neighborhood and worldwide cybersecurity polices, for example, the EU cybersecurity certification framework. It is mandatory for vendors and cell operators to comply with NESAS necessities.
How 5G Rewards Cloud-Indigenous Companies
With its lower latency, increased bandwidth, and considerable security measures, 5G strengthens the security of cloud connectivity. This up grade enables secure and dependable transmission of delicate information and facts as well as serious-time facts processing. 5G makes it possible for companies to confidently use cloud products and services to keep and manage their data, decreasing the risk of knowledge breaches.
5G delivers top-quality fault tolerance when in comparison to cable connections, mainly because of to the inherent resilience of wi-fi channels in mitigating interaction failures. With a cable connecting an business office or manufacturing unit to a service provider, it may well be needed to construct a backup relationship through an optical fiber or radio. But 5G has a reserved channel from the outset. If a person foundation station fails, others will consider around immediately, creating downtime not likely.
In addition, 5G network slicing capabilities present corporations with dedicated virtual networks inside of their IT program. This permits much better isolation and segregation of knowledge, purposes, and companies, bettering general security. Enterprises can build customized network slices for unique duties or specific departments. This feature ensures that critical details and programs continue to be different and protected.
Exactly where 5G Can Be Beneficial in Conjunction with the Cloud
Health care. Medical practitioners can use resources like a cloud AI platform to remotely monitor individual well being facts in genuine time though remaining cell by using 5G. Just after the health-related evaluation, superior-resolution health-related system pictures can be uploaded to the Cloud AI system, processed, and returned to a medical doctor for more use. 5G also helps with ML diagnostics: a cloud ML software can acquire visuals or other health care details over 5G for ailment prediction, detection, and classification.
Secure entry to company tools. With 5G details protection, obtain handle management is enabled for each SIM card. Licensed staff can securely access company electronic assets, info, and purposes though doing the job remotely without the need to have for a VPN or firewall is expected.
Streaming. With 5G and cloud companies like CDN, streamers, bloggers, and podcasters can take pleasure in uninterrupted, higher-top quality, stay online video and audio streaming. 5G facilitates the fusion of interactive things within are living video clip streams even though prompt video clip analytics produce true-time metrics that enrich the general are living celebration experience.
Intelligent factories. Producers can forecast servicing needs and detect potential problems or failures by monitoring equipment knowledge with IoT gadgets. They can use ML cloud products and services for analytics, whilst 5G presents a safe and rapidly relationship to their cloud infrastructure.
Automotive IoT. For the reason that of their performance capabilities, 5G networks are a excellent implies of knowledge transmission in industries. In the self-driving motor vehicle field, details from the vehicle’s sensors and cameras can be quickly sent to the cloud at substantial speeds, and then processed by cloud AI tools.
Gcore’s 5G eSIM System
The 5G eSIM system from the global cloud and CDN supplier Gcore delivers a highly effective case in point of a collaborative 5G and cloud alternative. The 5G eSIM system features entry to IaaS, PaaS, AI infrastructure, a streaming platform, and other Gcore services more than 5G. Gcore’s buyers can securely join to their cloud infrastructure by way of a direct private channel from more than 150 countries globally. 5G eSIM makes certain safe information transmission through advanced encryption algorithms and security protocols.
Here is the architecture of the platform:
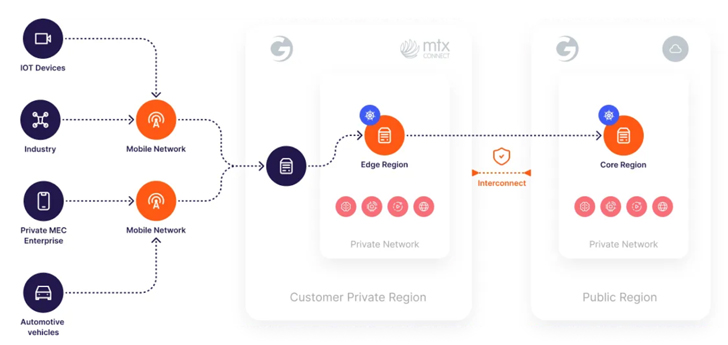 Determine 1. Gcore’s 5G eSIM System architecture
Determine 1. Gcore’s 5G eSIM System architecture
Aside from the 5G security features that are created-in in the typical, the 5G eSIM system offers:
- Regulate of traffic use for configuring a white listing and a black checklist. These allow for or deny specific protocols, URLs, and IPs.
- Workgroup administration for assigning employees’ names to eSIMs and grouping them by perform, seniority, or office.
- Comprehensive reporting technique to view the report by group, interval, eSIM, country, and far more.
- Own eSIMs for each and every employee to assign them a corporate cell quantity. Employees can obtain the internet and inner sources from a distant place without the will need for a corporate VPN and without the need of roaming expenses.
- Secured specific routing and targeted traffic filtering to guarantee defense against cyberattacks and knowledge leakage.
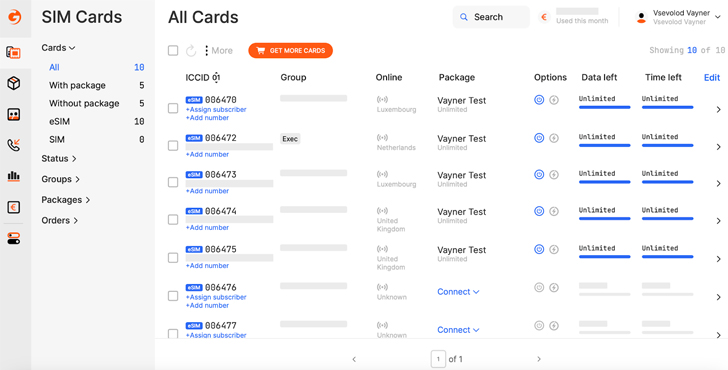 Figure 2. Gcore’s 5G eSIM regulate panel
Figure 2. Gcore’s 5G eSIM regulate panel
In addition, Gcore supplies functionality in its Cloud to secure all buyer products and services:
- Identification and entry management
- Firewall with versatile security team configuration
- Secrets management
- IaaS security
Consumers can blend these cloud options with the gains and functions provided by the 5G eSIM system.
Summary
5G has excellent performance abilities and state-of-the-art security functions this sort of as encryption, network slicing, and 5G AKA. 5G networks are a lot more resilient and versatile than LAN and WLAN networks this helps make 5G far more powerful in terms of technological breakthroughs, organization pursuits, and compliance with security requirements. As a outcome, 5G networks support businesses evolve more quickly without lessening the stage of infrastructure safety.
Located this post appealing? Stick to us on Twitter and LinkedIn to study extra unique material we publish.
Some parts of this article are sourced from:
thehackernews.com


 The best gifts for teachers
The best gifts for teachers