As a lot of as 34 Russian-speaking gangs distributing facts-stealing malware beneath the stealer-as-a-assistance model stole no fewer than 50 million passwords in the 1st 7 months of 2022.
“The underground sector value of stolen logs and compromised card aspects is approximated about $5.8 million,” Singapore-headquartered Team-IB explained in a report shared with The Hacker News.
Aside from looting passwords, the stealers also harvested 2.11 billion cookie information, 113,204 crypto wallets, and 103,150 payment cards.
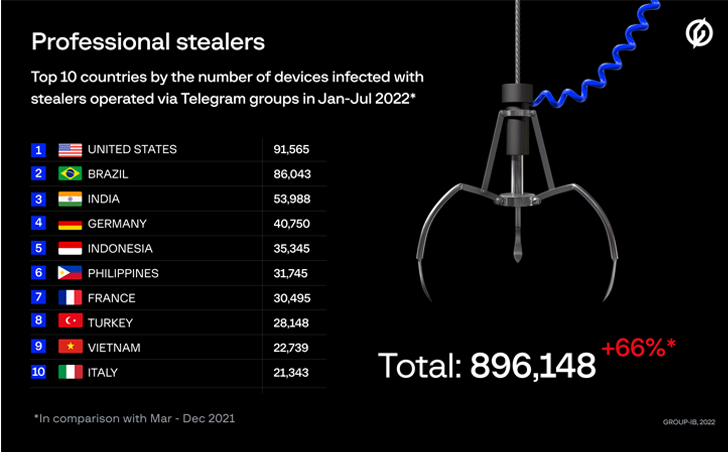
A majority of the victims are found in the U.S., followed by Brazil, India, Germany, Indonesia, the Philippines, France, Turkey, Vietnam, and Italy. In complete, 890,000 devices in 111 nations were contaminated in the course of the time body.
Team-IB said the members of quite a few fraud teams who are propagating the information stealers beforehand participated in the Classiscam procedure.
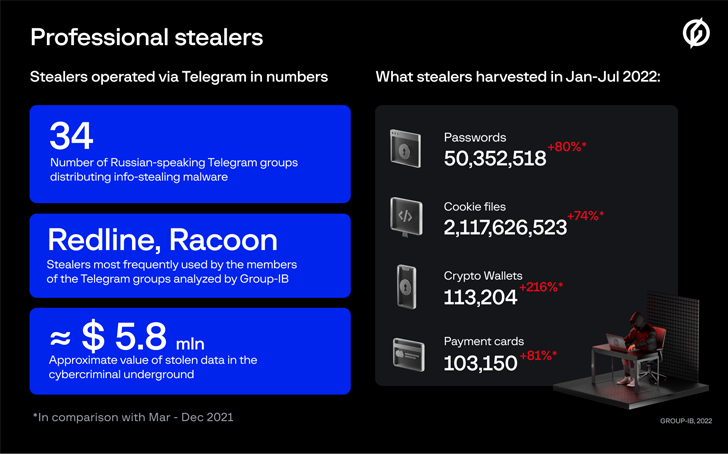
These groups, which are active on Telegram and have about 200 associates on ordinary, are hierarchical, consisting of administrators and workers (or traffers), the latter of whom are accountable for driving unsuspecting users to data-stealers like RedLine and Raccoon.
This is realized by location up bait websites that impersonate well-known firms and luring victims into downloading destructive information. Links to these kinds of internet sites are, in convert, embedded into YouTube movie opinions for well-known game titles and lotteries on social media, or shared instantly with NFT artists.
“Directors usually give employees each RedLine and Racoon in trade for a share of the stolen details or cash,” the firm mentioned. “Some teams use 3 stealers at the same time, while other people have only a person stealer in their arsenal.”
Pursuing a prosperous compromise, the cyber criminals peddle the stolen data on the dark web for monetary gain.
The progress highlights the very important purpose played by Telegram in facilitating a vary of prison actions, including performing as a hub for saying product or service updates, providing consumer help, and exfiltrating data from compromised devices.
The results also adhere to a new report from SEKOIA, which disclosed that seven diverse traffers groups have extra an up-and-coming data stealer acknowledged as Aurora to their toolset.
“The popularity of techniques involving stealers can be defined by the very low entry barrier,” Group-IB explained. “Inexperienced persons do not will need to have highly developed technological understanding as the method is entirely automated and the worker’s only job is to produce a file with a stealer in the Telegram bot and drive targeted visitors to it.”
Located this post attention-grabbing? Stick to THN on Facebook, Twitter and LinkedIn to read through much more special articles we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Ducktail Malware Operation Evolves with New Malicious Capabilities
Ducktail Malware Operation Evolves with New Malicious Capabilities