An unidentified danger actor has been noticed publishing typosquat packages to the Python Package Index (PyPI) repository for nearly 6 months with an goal to produce malware able of attaining persistence, thieving sensitive details, and accessing cryptocurrency wallets for fiscal gain.
The 27 deals, which masqueraded as well-liked genuine Python libraries, captivated countless numbers of downloads, Checkmarx stated in a new report. A the vast majority of the downloads originated from the U.S., China, France, Hong Kong, Germany, Russia, Eire, Singapore, the U.K., and Japan.
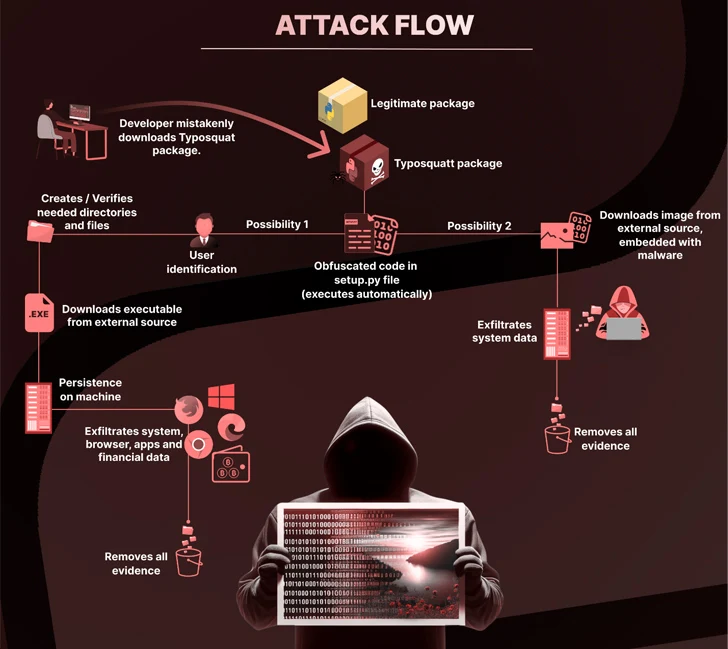
“A defining characteristic of this attack was the utilization of steganography to hide a destructive payload within an innocent-looking image file, which increased the stealthiness of the attack,” the software source chain security business stated.
Some of the offers are pyefflorer, pyminor, pyowler, pystallerer, pystob, and pywool, the previous of which was planted on May perhaps 13, 2023.
A widespread denominator to these packages is the use of the setup.py script to incorporate references to other destructive offers (i.e., pystob and pywool) that deploy a Visual Basic Script (VBScript) in order to down load and execute a file named “Runtime.exe” to reach persistence on the host.

Embedded in just the binary is a compiled file that’s capable of accumulating info from web browsers, cryptocurrency wallets, and other apps.
An alternate attack chain observed by Checkmarx is stated to have concealed the executable code in just a PNG graphic (“uwu.png”), which is subsequently decoded and run to extract the public IP handle and the universally exclusive identifier (UUID) of the affected procedure.
Pystob and Pywool, in unique, ended up printed less than the guise of equipment for API management, only to exfiltrate the information to a Discord webhook and endeavor to manage persistence by positioning the VBS file in the Windows startup folder.
“This marketing campaign serves as a further stark reminder of the at any time-current threats that exist in modern digital landscape, specially in regions in which collaboration and open up trade of code are foundational,” Checkmarx explained.
The enhancement comes as ReversingLabs uncovered a new wave of protestware npm deals that “disguise scripts broadcasting messages of peace similar to the conflicts in Ukraine and in Israel and the Gaza Strip.”
One of the offers, named @snyk/sweater-comb (model 2.1.1), determines the geographic spot of the host, and if it really is observed to be Russia, displays a message criticizing the “unjustified invasion” of Ukraine by means of another module known as “es5-ext”
An additional package deal, e2eakarev, has the description “no cost palestine protest deal” in the package.json file, and carries out related checks to see if the IP deal with resolves to Israel, and if so, log what is actually explained as a “harmless protest concept” that urges developers to elevate recognition about the Palestinian struggle.
It’s not just danger actors infiltrating open-source ecosystems. Earlier this 7 days, GitGuardian unveiled the existence of 3,938 whole exceptional secrets and techniques throughout 2,922 PyPI tasks, of which 768 exceptional secrets have been located to be legitimate.
This incorporates AWS keys, Azure Active Listing API keys, GitHub OAuth application keys, Dropbox keys, SSH keys, and credentials linked with MongoDB, MySQL, PostgreSQL, Coinbase and Twilio.

What’s much more, numerous of these secrets had been leaked more than when, spanning multiple release versions, bringing the full variety of occurrences to 56,866.
“Exposing tricks in open-source deals carries important pitfalls for developers and end users alike,” GitGuardian’s Tom Forbes said. “Attackers can exploit this data to attain unauthorized obtain, impersonate package deal maintainers, or manipulate users by way of social engineering practices.”
The continual wave of attacks targeting the application offer chain has also prompted the U.S. federal government to issue new direction this month for software program builders and suppliers to retain and present consciousness about software security.
“It is recommended that acquisition organizations assign offer chain risk assessments to their buying conclusions given the recent significant profile application supply chain incidents,” the Cybersecurity and Infrastructure Security Agency (CISA), Nationwide Security Agency (NSA), and the Place of work of the Director of Nationwide Intelligence (ODNI) claimed.
“Program builders and suppliers must improve their program progress procedures and lower the risk of damage to not just workers and shareholders, but also to their people.”
Located this report fascinating? Observe us on Twitter and LinkedIn to browse additional exclusive information we article.
Some parts of this article are sourced from:
thehackernews.com


 U.S. Cybersecurity Agencies Warn of Scattered Spider’s Gen Z Cybercrime Ecosystem
U.S. Cybersecurity Agencies Warn of Scattered Spider’s Gen Z Cybercrime Ecosystem