An Android malware campaign concentrating on Iranian financial institutions has expanded its capabilities and integrated further evasion methods to fly beneath the radar.
That’s in accordance to a new report from Zimperium, which identified a lot more than 200 destructive applications affiliated with the destructive operation, with the risk actor also observed carrying out phishing attacks versus the focused monetary establishments.
The marketing campaign very first came to light-weight in late July 2023 when Sophos comprehensive a cluster of 40 credential-harvesting apps targeting customers of Lender Mellat, Financial institution Saderat, Resalat Bank, and Central Bank of Iran.
The main objective of the bogus applications is to trick victims into granting them extensive permissions as nicely as harvest banking login qualifications and credit card facts by abusing Android’s accessibility providers.
“The corresponding respectable variations of the malicious applications are readily available at Cafe Bazaar, an Iranian Android marketplace, and have hundreds of thousands of downloads,” Sophos researcher Pankaj Kohli said at the time.

“The malicious imitations, on the other hand, were being readily available to download from a significant number of somewhat new domains, some of which the danger actors also employed as C2 servers.”
Curiously, some of these domains have also been noticed to provide HTML phishing webpages made to steal qualifications from mobile buyers.
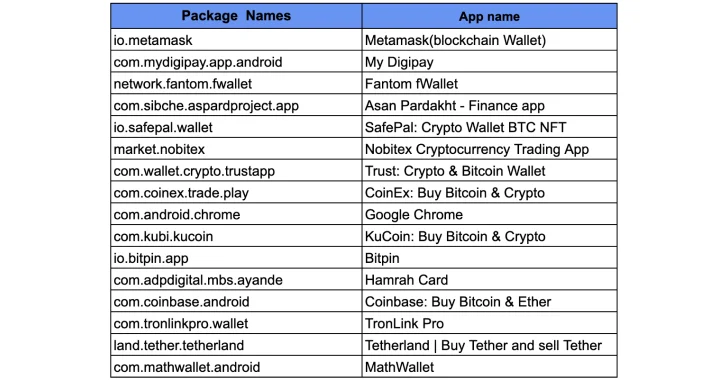
The latest results from Zimperium illustrate ongoing evolution of the threat, not only in conditions of a broader established of qualified banking institutions and cryptocurrency wallet apps, but also incorporating beforehand undocumented capabilities that make it additional strong.
This includes the use of the accessibility company to grant it more permissions to intercept SMS messages, protect against uninstallation, and simply click on person interface aspects.
Some variants of the malware have also been discovered to obtain a README file inside GitHub repositories to extract a Base64-encoded version of the command-and-control (C2) server and phishing URLs.
“This makes it possible for attackers to rapidly reply to phishing web pages currently being taken down by updating the GitHub repository, ensuring that malicious apps are generally obtaining the latest energetic phishing web-site,” Zimperium scientists Aazim Yaswant and Vishnu Pratapagiri stated.
Another noteworthy tactic is the use of intermediate C2 servers to host text information that contain the encoded strings pointing to the phishing sites.
While the marketing campaign has so considerably qualified its eyes on Android, there is evidence that Apple’s iOS operating method is also a possible goal primarily based on the fact that the phishing internet sites verify if the site is opened by an iOS unit, and if so, direct the target to a web site mimicking the iOS model of the Financial institution Saderat Iran app.
It is really at the moment not very clear if the iOS marketing campaign is beneath improvement stages, or if the applications are dispersed via an, as of nonetheless, unknown resource.

The phishing strategies are no significantly less refined, impersonating the precise web sites to exfiltrate credentials, account numbers, device styles, and IP addresses to two actor-managed Telegram channels.
“It is obvious that modern malware is getting to be extra refined, and targets are growing, so runtime visibility and safety are crucial for cell applications,” the scientists said.
The improvement arrives a little in excess of a month just after Fingerprint shown a strategy by which malicious Android applications can stealthily entry and copy clipboard details by leveraging the Technique_Warn_WINDOW permission to obscure the toast notification that’s exhibited when a unique application is reading through clipboard info.
“It really is probable to overdraw a toast possibly with a various toast or with any other look at, absolutely hiding the primary toast can stop the user from staying notified of clipboard steps,” Fingerprint said. “Any software with the Technique_Notify_WINDOW permission can study clipboard information without the need of notifying the user.”
Found this short article exciting? Comply with us on Twitter and LinkedIn to study much more exceptional information we publish.
Some parts of this article are sourced from:
thehackernews.com


 Discover Why Proactive Web Security Outsmarts Traditional Antivirus Solutions
Discover Why Proactive Web Security Outsmarts Traditional Antivirus Solutions