As a lot of as 350,000 open up resource jobs are considered to be perhaps vulnerable to exploitation as a consequence of a security flaw in a Python module that has remained unpatched for 15 decades.
The open up supply repositories span a quantity of business verticals, these types of as computer software advancement, artificial intelligence/equipment understanding, web development, media, security, IT management.
The shortcoming, tracked as CVE-2007-4559 (CVSS rating: 6.8), is rooted in the tarfile module, profitable exploitation of which could lead to code execution from an arbitrary file produce.

“The vulnerability is a route traversal attack in the extract and extractall capabilities in the tarfile module that enable an attacker to overwrite arbitrary files by including the ‘..’ sequence to filenames in a TAR archive,” Trellix security researcher Kasimir Schulz stated in a writeup.
At first disclosed in August 2007, the bug has to do with how a specifically crafted tar archive can be leveraged to overwrite arbitrary documents on a target machine merely on opening the file.
Place simply, a danger actor can exploit the weakness by uploading a destructive tarfile in a manner that tends to make it feasible to escape the listing that a file is intended to be extracted to and accomplish code execution, enabling the adversary to probably seize manage of a focus on unit.
“Hardly ever extract archives from untrusted sources without prior inspection,” the Python documentation for tarfile reads. “It is feasible that documents are designed outdoors of path, e.g. members that have complete filenames starting off with “https://thehackernews.com/” or filenames with two dots ‘..’.”

The vulnerability is also reminiscent of a just lately disclosed vulnerability in RARlab’s UnRAR utility (CVE-2022-30333) that could lead to distant code execution.
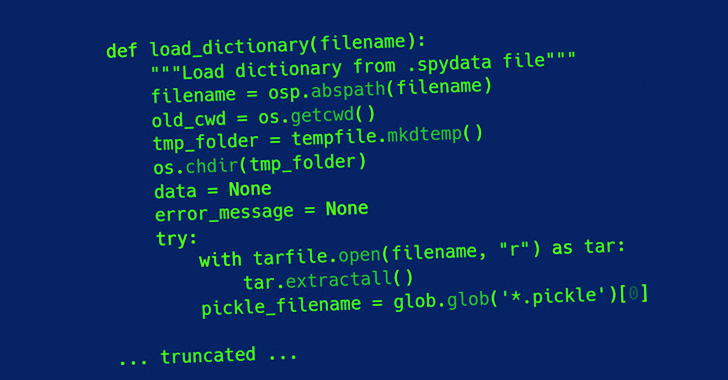
Trellix has additional produced a customized utility identified as Creosote to scan for projects susceptible to CVE-2007-4559, working with it to uncover the vulnerability in the Spyder Python IDE as very well as Polemarch.
“Left unchecked, this vulnerability has been unintentionally added to hundreds of countless numbers of open up- and closed-resource jobs globally, building a substantial software program source chain attack area,” Douglas McKee observed.
Identified this report appealing? Observe THN on Fb, Twitter and LinkedIn to examine a lot more unique information we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Volvo will unveil the electric EX90 SUV on November 9th
Volvo will unveil the electric EX90 SUV on November 9th