A established of 15 high-severity security flaws have been disclosed in the CODESYS V3 application development package (SDK) that could result in distant code execution and denial-of-provider under particular disorders, posing threats to operational technology (OT) environments.
The flaws, tracked from CVE-2022-47379 by way of CVE-2022-47393 and dubbed CoDe16, carry a CVSS rating of 8.8 with the exception of CVE-2022-47391, which has a severity ranking of 7.5. Twelve of the flaws are buffer overflow vulnerabilities.
“Exploitation of the found vulnerabilities, which influence all variations of CODESYS V3 prior to model 3.5.19., could put operational technology (OT) infrastructure at risk of assaults, this sort of as distant code execution (RCE) and denial-of-service (DoS),” Vladimir Tokarev of the Microsoft Threat Intelligence Neighborhood explained in a report.
Although a successful weaponization of the flaws demands user authentication as perfectly as an in-depth know-how of the proprietary protocol of CODESYS V3, the issues could have severe impacts that could final result in shutdowns and malicious tampering of critical automation processes.

The remote code execution bugs, in distinct, could be abused to backdoor OT gadgets and interfere with the functioning of programmable logic controllers (PLCs) in a way that could pave the way for details theft.
“Exploiting the vulnerabilities involves person authentication as properly as bypassing the Info Execution Prevention (DEP) and Handle Space Structure Randomization (ASLR) used by both equally the PLCs,” Tokarev discussed.
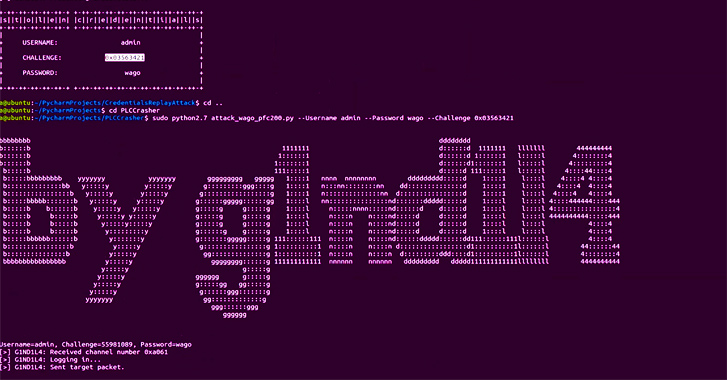
To get past the user authentication barrier, a acknowledged vulnerability (CVE-2019-9013, CVSS score: 8.8) is utilised to steal credentials by means of a replay attack in opposition to the PLC, adopted by leveraging the flaws to induce a buffer overflow and get command of the unit.
Patches for the flaws ended up introduced in April 2023. A transient description of the issues is as follows –
- CVE-2022-47379 – Immediately after prosperous authentication, particular crafted conversation requests can cause the CmpApp element to compose attacker-controlled knowledge to memory, which can direct to a denial-of-services situation, memory overwriting, or remote code execution.
- CVE-2022-47380 and CVE-2022-47381 – After thriving authentication, unique crafted conversation requests can bring about the CmpApp part to publish attacker-managed knowledge to stack, which can lead to a denial-of-assistance affliction, memory overwriting, or distant code execution.
- CVE-2022-47382, CVE-2022-47383, CVE-2022-47384, CVE-2022-47386, CVE-2022-47387, CVE-2022-47388, CVE-2022-47389, and CVE-2022-47390 – Right after successful authentication, distinct crafted interaction requests can bring about the CmpTraceMgr element to create attacker-managed information to stack, which can lead to a denial-of-assistance ailment, memory overwriting, or remote code execution.
- CVE-2022-47385 – Soon after thriving authentication, precise crafted interaction requests can lead to the CmpAppForce component to write attacker-managed details to stack, which can direct to a denial-of-service problem, memory overwriting, or distant code execution.
- CVE-2022-47391 – Crafted conversation requests can induce the affected products and solutions to examine internally from an invalid tackle, most likely primary to a denial-of-provider situation.
- CVE-2022-47392 – Just after prosperous authentication, certain crafted interaction requests with inconsistent information can result in the CmpApp/CmpAppBP/CmpAppForce components to go through internally from an invalid tackle, likely main to a denial-of-services problem.
- CVE-2022-47393 – Following successful authentication, specific crafted communication requests can induce the CmpFiletransfer element to dereference addresses provided by the request for inside study access, which can lead to a denial-of-assistance scenario.
“With CODESYS staying made use of by numerous sellers, one vulnerability could have an affect on many sectors, product varieties, and verticals, permit by itself several vulnerabilities,” Tokarev mentioned.
“Danger actors could launch a DoS attack in opposition to a machine using a susceptible model of CODESYS to shut down industrial functions or exploit the RCE vulnerabilities to deploy a backdoor to steal sensitive details, tamper with operations, or force a PLC to run in a perilous way.”
Observed this posting attention-grabbing? Follow us on Twitter and LinkedIn to read much more unique information we article.
Some parts of this article are sourced from:
thehackernews.com

 CISA Adds Microsoft .NET Vulnerability to KEV Catalog Due to Active Exploitation
CISA Adds Microsoft .NET Vulnerability to KEV Catalog Due to Active Exploitation