As the electronic age evolves and carries on to form the business enterprise landscape, corporate networks have develop into increasingly complex and distributed. The quantity of information a organization collects to detect destructive behaviour continually improves, producing it complicated to detect deceptive and unfamiliar attack styles and the so-called “needle in the haystack”. With a expanding quantity of cybersecurity threats, these as facts breaches, ransomware assaults, and destructive insiders, businesses are experiencing important challenges in successfully checking and securing their networks. In addition, the expertise scarcity in the industry of cybersecurity makes manual threat searching and log correlation a cumbersome and tough job. To address these issues, organizations are turning to predictive analytics and Machine Understanding (ML) driven network security solutions as essential equipment for securing their networks in opposition to cyber threats and the not known bad.
The Position of ML-Pushed Network Security Answers
ML-pushed network security answers in cybersecurity refer to the use of self-understanding algorithms and other predictive systems (data, time examination, correlations and so on.) to automate a variety of elements of menace detection. The use of ML algorithms is starting to be progressively popular for scalable technologies thanks to the restrictions existing in classic rule-dependent security solutions. This success in the processing of info by highly developed algorithms that can discover designs, anomalies, and other subtle indicators of malicious action, like new and evolving threats that could not have regarded terrible indicators or present signatures.
Detecting regarded threat indicators and blocking proven attack designs is still a very important aspect of total cyber cleanliness. Nonetheless, regular strategies making use of threat feeds and static principles can come to be time-consuming when it comes to preserving and masking all the unique log resources. In addition, Indicators of Attack (IoA) or Indicators of Compromise (IoC) may possibly not be readily available at the time of an attack or are rapidly outdated. As a result, providers have to have other ways to fill this gap in their cybersecurity posture.
In summary, the talked about disadvantages of rule-based mostly security alternatives highlight the importance of taking a more holistic tactic to network security, which need to presently involve ML-driven Network Detection and Response (NDR) solutions to enhance regular detection capabilities and preventive security steps.
The Positive aspects of ML for Network Security
So, how is Machine Learning (ML) shaping the future of network security? The real truth is ML-driven security methods are bringing about a sizeable transformation in network security by offering security groups with several advantages and enhancing the all round menace detection capabilities of organizations:
- Massive information analytics:With the ever-expanding sum of facts and distinct log sources, organisations will have to be able to procedure huge amounts of info in true-time, together with network targeted traffic logs, endpoints, and other sources of data connected to cyber threats. In this regard, ML algorithms can aid in the detection of security threats by figuring out styles and anomalies that may well normally go unnoticed. As a result, the ability and adaptability of a solution to include distinct log sources really should be a key requirement for danger detection capabilities.
- Automated examination of anomalous conduct: AI allows a substantially-necessary health and fitness checking of network activity by utilising the evaluation of standard network targeted visitors as a baseline. With the aid of automated correlation and clustering, outliers and abnormal behavior can be detected, decreasing the want for manual detection engineering and danger searching. Important questions to be answered incorporate “what is the action of other shoppers in the network?” and “is a client’s habits in line with its own former routines?” These strategies allow for for the detection of abnormal behaviors like domain-produced algorithms (DGA) domains, quantity-dependent irregularities in network connections, and unconventional communication patterns (e.g., lateral movement) in the network. Thus, comparing a client’s present-day actions with that of its friends serves as a appropriate baseline for figuring out subtle anomalies.
- Detect unknown assaults in genuine-time: Whileit is relatively quick to immediately detect regarded undesirable indicators (distinct IP addresses, domains and so on.), quite a few attacks can go undetected when these indicators are not existing. If that is the situation, data, time and correlation-primarily based detections are of tremendous worth to detect unfamiliar attack designs in an automatic method. By incorporating algorithmic ways, traditional security alternatives based mostly on signatures and indicators of compromise (IoC) can be increased to turn out to be much more self-ample and much less reliant on recognised malware indicators.
- Self-discovering detection capabilities: ML-pushed methods master from earlier occasions in order to continuously improve their danger detection abilities, threat scoring, clustering and network visualisations. This may include training the algorithms them selves or adjusting how facts is offered based on responses from analysts.
- Boost Incident Response:By understanding from an analyst’s past incident response pursuits, ML can automate certain factors of the incident reaction system, minimizing the time and resources demanded to deal with a security breach. This can entail working with algorithms to review textual content and evidence, pinpointing root will cause and attack styles.
Instance of an ML-driven Network Security Alternative
When it comes to ML-pushed Network Detection & Reaction (NDR) solutions that incorporate the outlined rewards, ExeonTrace stands out as a leading network security solution in Europe. Based mostly on award-successful ML algorithms, which integrate a decade of educational investigation, ExeonTrace gives companies with innovative ML danger detection abilities, comprehensive network visibility, versatile log supply integration and massive knowledge analytics. In addition, the algorithms depend on metadata investigation as an alternative of genuine payloads which would make them unaffected by encryption, completely hardware-free and suitable with most cybersecurity infrastructures. As a outcome, ExeonTrace is equipped to procedure uncooked log data into effective graph databases, which are then analyzed by supervised and unsupervised ML-types. By way of correlation and occasion fusion, the algorithms can properly pinpoint superior-fidelity anomalies and refined cues of malicious behavior, even when working with novel or rising cyber threats that may well deficiency set up signatures or known destructive indicators.
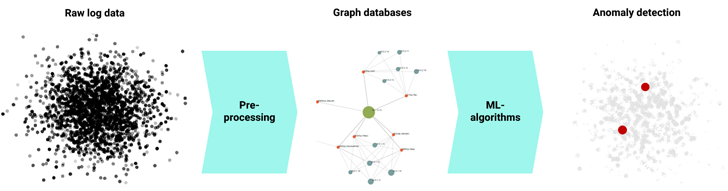 Security Analytics Pipeline: Detection of network anomalies via ML
Security Analytics Pipeline: Detection of network anomalies via ML
Conclusion
As the danger of cyber attacks will become more and more complex, companies should go outside of common security steps to defend their networks. As a end result, numerous firms are now turning to Equipment Learning (ML) and predictive analytics to reinforce their security defenses. In this regard, ML-driven Network Detection & Response (NDR) options, these kinds of as ExeonTrace, are designed to support organizations stay ahead of the ever-evolving risk landscape. By making use of sophisticated ML algorithms that analyze network targeted visitors and software logs, ExeonTrace gives organizations brief detection and response to even the most advanced cyberattacks.
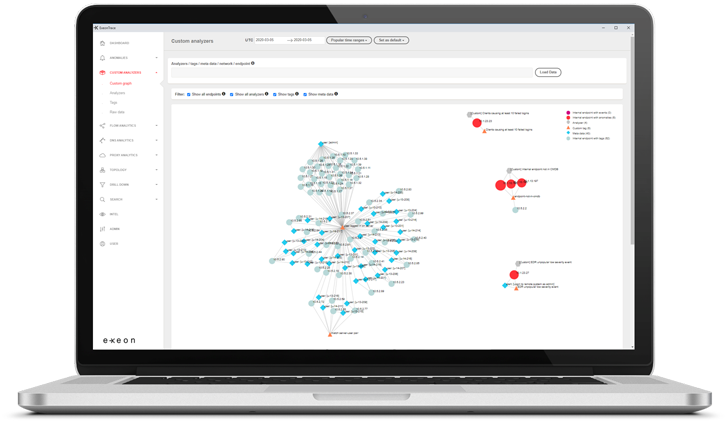 ExeonTrace Platform: Network visibility
ExeonTrace Platform: Network visibility
E-book a no cost demo to discover how ExeonTrace leverages ML algorithms to make your organisation much more cyber resilient – rapidly, trustworthy and fully components-cost-free.
Identified this short article appealing? Stick to us on Twitter and LinkedIn to read extra unique material we article.
Some parts of this article are sourced from:
thehackernews.com


 City Fund Managers Jailed for $8m Fraud
City Fund Managers Jailed for $8m Fraud