Information have emerged about a now-patched vulnerability in Azure Service Fabric Explorer (SFX) that could direct to unauthenticated distant code execution.
Tracked as CVE-2023-23383 (CVSS score: 8.2), the issue has been dubbed “Tremendous FabriXss” by Orca Security, a nod to the FabriXss flaw (CVE-2022-35829, CVSS rating: 6.2) that was preset by Microsoft in October 2022.
“The Super FabriXss vulnerability enables distant attackers to leverage an XSS vulnerability to obtain remote code execution on a container hosted on a Service Fabric node without the need of the will need for authentication,” security researcher Lidor Ben Shitrit explained in a report shared with The Hacker News.
XSS refers to a sort of shopper-side code injection attack that would make it achievable to add malicious scripts into or else dependable web-sites. The scripts then get executed each time a target visits the compromised website, thereby leading to unintended consequences.
Though each FabriXss and Tremendous FabriXss are XSS flaws, Super FabriXss has a lot more intense implications in that it could be weaponized to execute code and likely get handle of susceptible programs.
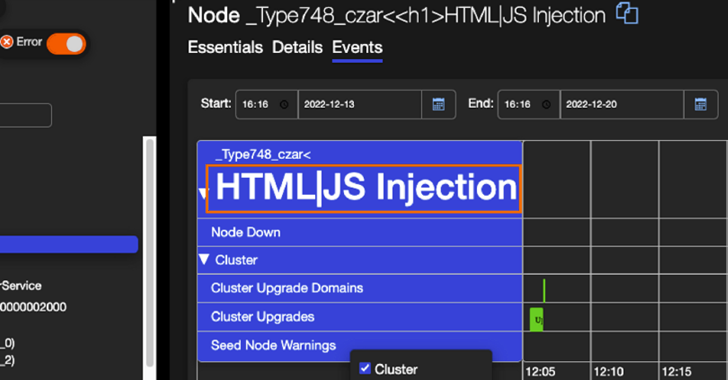
Super FabriXss, which resides in the “Situations” tab involved with every single node in the cluster from the consumer interface, is also a mirrored XSS flaw, this means the script is embedded into a connection, and is only activated when the website link is clicked.
“This attack can take edge of the Cluster Type Toggle selections less than the Occasions Tab in the Service Material platform that lets an attacker to overwrite an current Compose deployment by triggering an up grade with a specifically crafted URL from XSS Vulnerability,” Ben Shitrit explained.
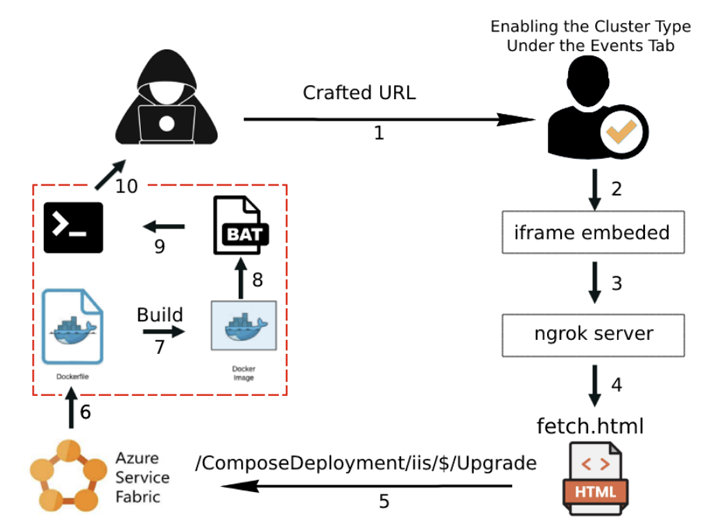
“By using control of a respectable software in this way, the attacker can then use it as a platform to start further assaults or attain obtain to sensitive facts or assets.”
The flaw, in accordance to Orca, impacts Azure Assistance Material Explorer variation 9.1.1436.9590 or before. It has since been addressed by Microsoft as section of its March 2023 Patch Tuesday update, with the tech big describing it as a spoofing vulnerability.
“The vulnerability is in the web customer, but the destructive scripts executed in the victim’s browser translate into actions executed in the (distant) cluster,” Microsoft observed in its advisory. “A victim person would have to click the saved XSS payload injected by the attacker to be compromised.”
THN WEBINARBecome an Incident Response Pro!
Unlock the techniques to bulletproof incident response – Master the 6-Section method with Asaf Perlman, Cynet’s IR Leader!
Do not Skip Out – Help save Your Seat!
The disclosure arrives as NetSPI exposed a privilege escalation flaw in Azure Operate Applications, enabling people with “browse only” permissions to obtain sensitive information and facts and gain command execution.
It also follows the discovery of a misconfiguration in Azure Active Listing that exposed a range of programs to unauthorized access, including a content material administration program (CMS) that powers Bing.com.
Cloud security company Wiz, which codenamed the attack BingBang, explained it could be weaponized to alter lookup effects in Bing, and worse, even carry out XSS assaults on its consumers.
Located this short article interesting? Follow us on Twitter and LinkedIn to study additional unique information we submit.
Some parts of this article are sourced from:
thehackernews.com

 North Korean Hackers Use Trojanized 3CX DesktopApp in Supply Chain Attacks
North Korean Hackers Use Trojanized 3CX DesktopApp in Supply Chain Attacks