U.S. Treasury Sanctions Iranian Firms and Individuals Tied to Cyber Attacks
The U.S. Treasury Department’s Business office of Foreign Assets Regulate (OFAC) on Monday sanctioned two companies and 4 persons for their involvement in destructive cyber things to do on behalf of the Iranian Islamic Revolutionary Guard…
U.S. Treasury Sanctions Iranian Firms and Individuals Tied to Cyber AttacksRead More
Researchers Detail Multistage Attack Hijacking Systems with SSLoad, Cobalt Strike
Cybersecurity scientists have identified an ongoing attack campaign which is leveraging phishing e-mail to provide malware named SSLoad. The campaign, codenamed FROZEN#SHADOW by Securonix, also requires the deployment of Cobalt Strike and the ConnectWise ScreenConnect distant…
Researchers Detail Multistage Attack Hijacking Systems with SSLoad, Cobalt StrikeRead More

Major Security Flaws Expose Keystrokes of Over 1 Billion Chinese Keyboard App Users
Security vulnerabilities uncovered in cloud-based pinyin keyboard apps could be exploited to reveal users’ keystrokes to nefarious actors. The results occur from the Citizen Lab, which found weaknesses in 8 of nine apps from vendors like…
Major Security Flaws Expose Keystrokes of Over 1 Billion Chinese Keyboard App UsersRead More

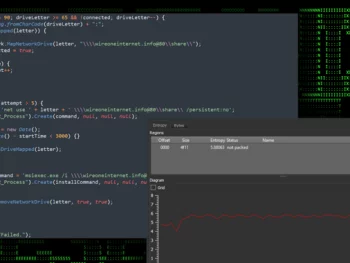
eScan Antivirus Update Mechanism Exploited to Spread Backdoors and Miners
A new malware campaign has been exploiting the updating mechanism of the eScan antivirus computer software to distribute backdoors and cryptocurrency miners like XMRig through a long-standing menace codenamed GuptiMiner concentrating on substantial company networks. Cybersecurity…
eScan Antivirus Update Mechanism Exploited to Spread Backdoors and MinersRead More
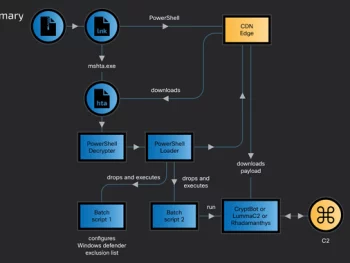
CoralRaider Malware Campaign Exploits CDN Cache to Spread Info-Stealers
A new ongoing malware marketing campaign has been noticed distributing three different stealers, these as CryptBot, LummaC2, and Rhadamanthys hosted on Content Shipping Network (CDN) cache domains considering the fact that at least February 2024. Cisco…
CoralRaider Malware Campaign Exploits CDN Cache to Spread Info-StealersRead More

Apache Cordova App Harness Targeted in Dependency Confusion Attack
Scientists have determined a dependency confusion vulnerability impacting an archived Apache challenge named Cordova App Harness. Dependency confusion attacks consider location owing to the actuality that package deal managers check the general public repositories ahead of…
Apache Cordova App Harness Targeted in Dependency Confusion AttackRead More