Facts have emerged about a not long ago patched critical remote code execution vulnerability in the V8 JavaScript and WebAssembly engine applied in Google Chrome and Chromium-centered browsers.
The issue relates to a case of use-after-free of charge in the instruction optimization ingredient, effective exploitation of which could “allow an attacker to execute arbitrary code in the context of the browser.”
The flaw, which was identified in the Dev channel version of Chrome 101, was documented to Google by Weibo Wang, a security researcher at Singapore cybersecurity business Numen Cyber Technology and has considering that been quietly set by the corporation.

“This vulnerability happens in the instruction selection stage, where the improper instruction has been picked and resulting in memory obtain exception,” Wang claimed.
Use-after-absolutely free flaws manifest when past-freed memory is accessed, inducing undefined behavior and triggering a software to crash, use corrupted info, or even attain execution of arbitrary code.
What is more regarding is that the flaw can be exploited remotely through a specially built web-site to bypass security limitations and operate arbitrary code to compromise the qualified techniques.
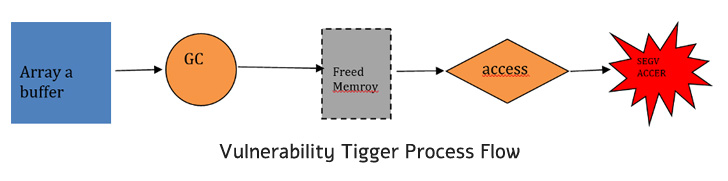
“This vulnerability can be even further exploited employing heap spraying procedures, and then qualified prospects to ‘type confusion’ vulnerability,” Wang defined. “The vulnerability makes it possible for an attacker to control the functionality pointers or produce code into arbitrary destinations in memory, and in the end lead to code execution.”
The firm has not nevertheless disclosed the vulnerability via the Chromium bug tracker portal to give as quite a few people as feasible to install the patched edition initial. Also, Google does not assign CVE IDs for vulnerabilities uncovered in non-stable Chrome channels.

Chrome customers, especially builders who use the Dev version of Chrome for testing to assure that their apps are compatible with the most recent Chrome features and API modifications, must update to the hottest out there edition of the application.
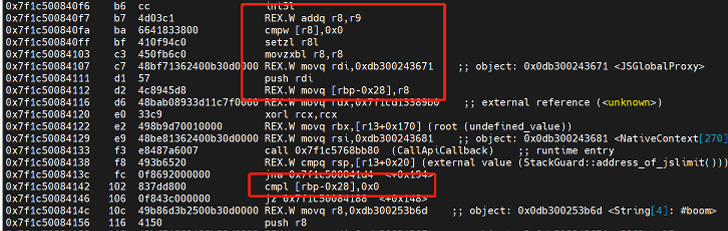 TurboFan assembly directions immediately after vulnerability patched
TurboFan assembly directions immediately after vulnerability patched
This is not the first time use-just after-no cost vulnerabilities have been found in V8. Google in 2021 resolved 7 these kinds of bugs in Chrome that have been exploited in serious-planet attacks. This 12 months, it also fixed an actively exploited use-soon after-cost-free vulnerability in the Animation part.
Located this post attention-grabbing? Observe THN on Fb, Twitter and LinkedIn to read through much more unique content we put up.
Some parts of this article are sourced from:
thehackernews.com


 How to determine if you should install solar panels at home
How to determine if you should install solar panels at home