Apple has built structural enhancements in iOS 14 to block information-based, zero-simply click exploits.
In an effort to prevent attacks from staying launched by way of its iMessage feature, Apple has debuted a security services termed BlastDoor in iOS 14, its current cell operating process version.
1st in depth in an investigation this 7 days by Google Job Zero’s Samuel Groß, BlastDoor functions as a “tightly sandboxed” assistance that is accountable for “almost all” of the parsing of untrusted data in iMessages.
The assistance arrives on the heels of a a short while ago uncovered iMessage zero-simply click exploit, which was remaining leveraged in an espionage attack versus Al Jazeera journalists and executives. Citizen Lab, who disclosed the campaign in December, at the time stated it did not imagine that the exploit functions from iOS 14, as it “includes new security protections.”
Nonetheless, what these unique protections were being remained unknown right up until Groß’s investigation this week. Groß was ready to conduct reverse-engineering in get to analyze the new provider, using an M1 Mac Mini operating macOS 11.1, and verifying his conclusions by implementing them to iOS 14.3 (jogging on an iPhone XS),
“Overall, these improvements are likely extremely shut to the greatest that could’ve been carried out specified the will need for backwards compatibility, and they ought to have a important effect on the security of iMessage and the platform as a full,” explained Groß on Thursday. “It’s great to see Apple putting aside the assets for these types of significant refactorings to make improvements to finish users’ security.”
What is BlastDoor?
BlastDoor has two vital security implications.
1st, the services will allow sandboxing rules to be utilized throughout the pipeline when a information is acquired on a phone. This means that when a message is been given, the procedures on the backend execute code independently from the running method. Only two procedures (IMTransferAgent, which handles information file transfers, and apsd, Apple’s Drive Notification Service daemon) are needed to carry out network functions.
Groß reported the sandbox profile of BlashDoor is “quite tight,” with practically all file program interactions getting blocked, outbound network accessibility staying denied, and any conversation with IOKit motorists becoming forbidden. IOKit enables the obtain of components units and motorists for different applications and companies, and is historically a major source of vulnerabilities.
This safe ecosystem indicates that any destructive code despatched by attackers through iMessage is prevented from accessing person details or interacting with other elements of the operating system.
Second, BlastDoor is created in Swift, which is a memory-safe language. Groß stated that Swift makes it “significantly” more challenging to introduce memory-corruption vulnerabilities into the code base. That is for the reason that Swift has many attributes to make confident variables are initialized right before they are employed, memory is not accessed immediately after it’s been deallocated, and array indices are checked for out-of-bounds errors.
A New Concept-Parsing Process
In preceding variations of iOS, when a message was despatched, the parsing would occur in the Quick Messaging Agent (imagent). To parse a information in imagent, the binary info would initially be decompressed then the plist (also recognised as residence list an extension utilized to conserve tastes of programs) would be decoded from its binary serialization structure. The various fields would be extracted to be certain they have the appropriate sort and lastly, the `x` field articles of the iMessage structure would be decoded applying an XML decoder. If an iMessage contained an attachment, further steps would also be taken for parsing.
In iOS 14, this method has been moved to the new BlastDoor company. The primary processing stream even now commences in imagent – which receives the uncooked payload bytes, but then the messages are forwarded to the BlastDoor provider (via +[IMBlastdoor sendDictionary:withCompletionBlock:]). Inside BlastDoor, the processes of both of those parsing messages and attachments primarily manifest in BlastDoor.framework and MessagesBlastDoorService, reported Groß.
Groß noted that a person side result of this new processing pipeline is that imagent can now detect when an incoming concept caused a crash in BlastDoor – and appears to be informing Apple’s servers about these kinds of functions.
“It is unclear what the intent of this is without access to the server’s code,” said Groß. “While these notifications could simply just be used for statistical uses, they would also give Apple a fairly very clear signal about attacks against iMessage involving brute-power and a somewhat weaker signal about any failed exploits towards the BlastDoor services.”
Other iOS 14 Protections
In addition to BlastDoor, Groß drop mild on two other important security protections that were created into iOS 14, which was unveiled to the community in September.
Initial, Apple has mounted an issue with the shared cache location of its handle space structure randomization (ASLR) that was posing an architectural weakness. The weak spot stemmed from the shared caches region only randomizing for every boot – that means it would remain at the identical tackle across all procedures. This could have permitted attackers to infer the foundation address of the shared cache and split ASLR – probably placing them up to start zero-simply click attacks.
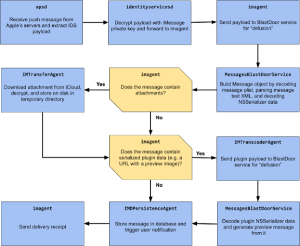
BlastDoor’s message parsing course of action (click on to enlarge). Credit rating: Google Challenge Zero
Apple has now included logic to particularly detect this kind of attack. Now, shared cache is re-randomized for the focused assistance during the up coming time it is started out, rendering this type of attack ineffective.
“This really should make bypassing ASLR in a -click attack context drastically more difficult or even unattainable (aside from brute pressure) depending on the concrete vulnerability,” reported Groß.
Next, the BlastDoor and imagent companies are now issue to a recently launched “exponential throttling mechanism” enforced by launchd, Apple’s functioning procedure support management daemon. With this new mechanism, if a crash takes place on the device, the intervals amongst restarts following the crash double with each subsequent crash (major to an interval maxing out at 20 minutes, Groß identified).
“With this improve, an exploit that relied on regularly crashing the attacked provider would now very likely require in the buy of a number of hours to approximately fifty percent a working day to complete instead of a handful of minutes,” reported Groß.
Apple Security Woes
Apple, historically recognized for its strong security posture, has confronted various issues about the previous several months – which includes the release of an crisis update this week to patch three zero-working day vulnerabilities uncovered in iOS.
Zero-click on attacks operate quickly with no any person conversation and are of individual fear. Researchers in August uncovered a zero-click on macOS exploit chain that could permit attackers to supply malware to macOS customers utilizing a Microsoft Business doc with macros.
Groß applauded Apple’s offensive security work reflected in the new changes, particularly for its influence from message-based mostly zero-simply click attacks.
“Not just solitary bugs had been mounted, but alternatively structural enhancements have been designed dependent on insights acquired from exploit advancement work,” he stated.
Threatpost has attained out to Apple for even further comment.
Obtain our exclusive No cost Threatpost Insider Book Healthcare Security Woes Balloon in a Covid-Period Environment , sponsored by ZeroNorth, to learn more about what these security threats indicate for hospitals at the working day-to-working day amount and how health care security teams can apply ideal procedures to guard vendors and people. Get the total story and Down load the E-book now – on us!
Some parts of this article are sourced from:
threatpost.com


 ZTE Axon 30 Pro might come with Samsung’s 200MP sensor
ZTE Axon 30 Pro might come with Samsung’s 200MP sensor